Nuking Data and Other Data Deletion Considerations
Nuking Data and Other Data Deletion Considerations
When I was in elementary school, my father and brother helped me build my first computer; I had scavenged the parts from the obsolete equipment my school was throwing out.
I had only the vaguest idea of what we were doing, but I distinctly remember firing up a word processor and finding several letters written by former teachers of mine still on the hard-drive. Unfortunately, this kind of leak is not unique.
Just yesterday, an acquaintance told me how he used to dumpster dive at a computer disposal plant and found several hard-drives from the Wisconsin Department of Justice. Unencrypted.
If one wanted to earn a profitable living as a “market researcher”, identity thief, or foreign intelligence agent, buying liquidated computer equipment or working for a photocopier leaser would be a good place to start. Recovering even so-called deleted data is relatively easy with off-the-shelf software and a little know-how.
This article attempts to first explain how data storage works, dispel some of the myths around data destruction, and then tell you how to actually blow that data into oblivion.
How Data Are Stored
Imagine a new hard-drive as a field covered in freshly fallen snow. At first it’s flat and empty, but when you walk across it, you leave footprints. You can obscure your tracks by walking over them, but you can’t put the snow back to its fresh, flat state.
Your hard-drive is not much different. Your hard-drive has a “file system” that is a schema for how to write the bits to the hard-drive’s sectors. This file system is like a table of contents that tells us SecretPlans.doc is stored in sectors 12, 33, and 91. When you “delete” a file, it simply removes the entry from the file system, and says that sectors 12, 33 and 91 are available to be written to again. Until those sectors are over-written, the data continue to exist and are recoverable through most recovery software.
Other kinds of storage media are not very different in that their deleted data are mostly recoverable. Flash drives operate in a similar way from a software perspective, but physically operate differently. Also, the storage on embedded devices, such as cell phones, can store things like deleted text messages and pictures, but the tools to recover them are varied and difficult to use. The recovery processes differs somewhat from magnetic media, but nonetheless is possible.
Unsecure Deletion and Myths
Empty the Recycle Bin
When you empty your recycle bin, all that does is remove the entries for those files. Recovery software can still go through and do what’s called file carving to search for data that is not yet overwritten. This can be especially handy when you deleted that precious baby photo from your camera or lost that thesis paper; it’s also handy to recover those medical records from that insurance company’s dumpster.
Reformatting
It’s a common misconception that “reformatting” a device destroys all the data. Reformatting simply means changing how the drive decides to write new data in a new schema. While it is true most operating systems will not recognize the data that was once there, it’s far from securely deleted. It’s analogous to ripping out a table of contents in a book and saying the whole novel was destroyed. A trained forensics analyst can re-create the old file system and recover the data.
File Deletion Tools
I consider most secure deletion software not comprehensive enough. It is true that file deletion utilities (such as Eraser for Windows or the “shred” for Linux) will overwrite the sectors of a file and make it unrecoverable. However, there are still plenty of other places for an analyst to look. For example, when Microsoft Word opens a file, it creates a temporary, hidden file that holds edits until you click “save”. That temp file, like any other, sits in that sector long after it’s been removed from the file system.
Also, most operating systems maintain what’s called swap space to augment RAM and give the computer more temporary workspace. This swap space (either a file or a separate partition) sits on the hard-drive, and can leave ghosts behind. Additionally, indexing services like Google Desktop or the Windows file system can leak other kinds of metadata, such as file names or even possibly thumbnails of pictures.
If you know what you are doing, tools like shred and Eraser can be extremely useful, but unless you want to track down and scrub all these breadcrumbs by hand, you can’t say for sure that a file is nowhere else to be found.
Scrubbing
Zeroing is the process of writing zeros to free sectors, and scrubbing is the practice of over-writing unused sectors with random data. There are paranoid recommendations abound for how many times a sector should be over-written (most famously the Gutmann method) but most of them are Internet urban legends.
People sometimes cite the Department of Defense NISP Operating Manual (5220.22-M) as saying three or seven passes of random data are the “standard”. The citations are vague and uncertain, but as of 28 June 2007, the military will only accept physical destruction of media as the data sanitization procedure for sensitive data. Security vendors like to throw around the word “military-grade” or “military standards” but it is mostly marketing; I’m sure there’s a military standard for spork vendors, but it doesn’t mean other sporks won’t do the job.
According to the National Institute of Standards and Technology’s Guidelines for Media Sanitization, “Studies have shown that most of today’s media can be effectively cleared by one overwrite.” To my knowledge, nobody has ever recovered data from a zeroed or scrubbed hard-disk. To do so would require thousands of dollars, access to clean room conditions and expensive scientific equipment (or some as-of-yet undisclosed technique). If the NSA or CIA can do it, they aren’t talking.
To scrub a large drive takes a long time, and so I have settled on three passes as an acceptable level. A single wipe is really all that is necessary, especially for my encrypted drives, but nine times out of ten it runs overnight and makes no difference to me. Also, it leaves you with that warm, fuzzy secure feeling.
Best Practices
There is a proper methodology to destroying data. I will list the steps below, but obviously your specific circumstances dictate how many are feasible.
Encrypt Your Data
In our previous article about file encryption we discuss how to protect your data on the hard-drive using free tools. Full-disk encryption works at the data-on-the-platter level, and will protect your data from ever being written to the drive in plain text. Furthermore, full-disk encryption even encrypts the unused space, so your actual data are indistinguishable from either free space or random data. If you don’t encrypt, you’ll always be playing catch-up with data destruction.
Minimize Data
When possible, keep the pieces of sensitive data that touch your machine to a minimum. That means don’t keep your entire medical history on your iPad or your bank records on a laptop that you don’t even do your banking on.
If you are going to be doing sensitive Internet browsing, use your browser’s private browsing feature. Internet Explorer’s InPrivate and Safari’s Private Browsing have some fundamental issues with their implementations of private browsing, so I do not recommend them. Mozilla Firefox’s Private Browsing and Chrome’s Incognito Mode store your cache and history in memory (not the hard-drive) and are wiped away when the private browsing is done or the machine rebooted.
Scrub Free Space
If your machine must run unencrypted, scrubbing free-space is not a bad idea. On the Windows side, I recommend Eraser, which has free space scrubbing built in. In Linux, the sfill command (and other tools) will do this for you. While I am not a Mac person, a tool called ShreadIt X seems to fit the bill. How often is up to you, but just remember that determined attackers will likely find something incriminating you left behind.
Please note that this step is unnecessary if your disk is encrypted.
Wipe the Disk
When you’re done with a device or going to repurpose it, you can nuke it clean using software; wiping software will go through each sector of your device and over-write it with random data, thereby blowing whatever was there into oblivion. There are other tools out there for this, but my favorite (free) tool is Darik’s Boot and Nuke (DBAN). Download the image, burn it to a CD, and boot from it.
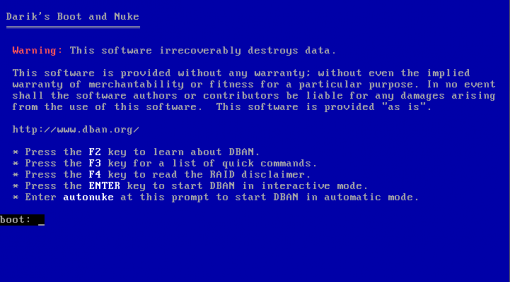
This is what it looks like when it first boots. If you just want the drive scrubbed, type “autonuke” and let it do the rest.
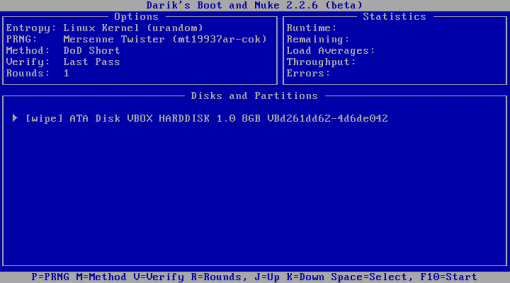
This is the interactive mode where you can choose which drives you are going to wipe. In this example, there is only a single 8 gigabyte hard-drive in my virtual machine.
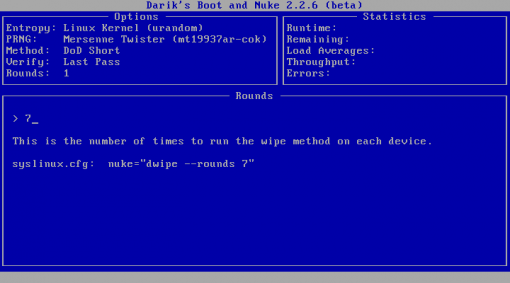
If you specify a method (by pressing M), you can choose the number of wipes. A single pass is safe, three is very secure, seven is paranoid, and more than that and you’re just shortening the life of your drive.
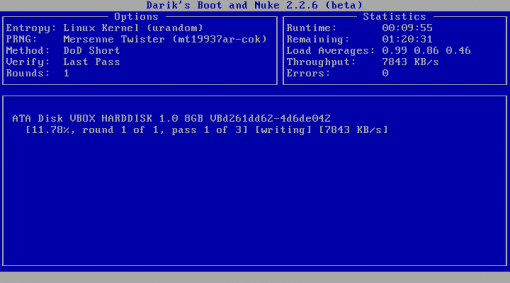
This is what it looks like running. Everything gets blown away, operating system included, so if you plan on donating or selling your machine be sure to reinstall the operating system or include the discs with the machine.
If you are in a commercial or regulated environment (such as a HIPPA-regulated company), than you may be forced to buy some kind of certified software based on your IT department’s recommendations. Because DBAN is open source, it can’t offer any kind of certification because it would constitute a warranty. If you run your own company or this is for your own machine, it will serve you well.
Shoot it or blow it up
Yep, you heard me. Open that hard-drive up, take out the powerful magnets as a toy and hit those platters with a hammer. Take them to the range and shoot them. Play with thermite and melt them into slag. Anything you do that even slightly damages the platters is going to stop virtually every attacker, and I’d love to someone try to recover data from a disk that’s taken a few .308.
While this is fun, it is especially necessary for all non-magnetic storage. One of my co-workers is a computer forensics analyst and has told me stories about recovering data from phones that people just cracked the screens in half, thinking it’s safe. It’s not just law enforcement and the military with this technology, the same software tools are available to the public for free or cheap, and the hardware is very inexpensive. If you are, in fact, the lucky subject of a federal investigation, they will shave the tops of your phone’s flash chips in microscopic layers and photograph the gates; from this they can reconstruct some of the data from the phone. Crazy stuff to be sure, but the phone is useless to anyone if it has been run over by one-too-many Ford F150’s.
Conclusion
While there are many attack vectors for a determined recovery agent, protecting yourself is relatively easy. It’s as simple as encrypt your data, and blow it away when you’re done using DBAN or your favorite Snap-On tool. It’s unlikely we can eliminate data leaks on the whole, but at least you don’t have to be another line in an identity thief’s spreadsheet-for-sale. The tools are there waiting for you, and it’s up to you to use them at work and at home.
Andrew Stuckey is a full-time geek who dabbles in online publishing, information security, and prepping for the end of the world. A graduate of the Wisconsin School of Business in Information Systems, he currently works in IT and in his spare time co-hosts the podcast You’re Wrong Here’s Why. For more fun facts, visit his website at andrewstuckey.com











Discussion