A Glimpse Into the Future of Digital Security at the RSA Conference 2017
A Glimpse Into the Future of Digital Security at the RSA Conference 2017
Every February, the flagship RSA Conference comes to San Francisco. It brings with it a bevy of cryptography and information security companies displaying their wares to other security companies, vendors, resellers, corporate information security and information technology personnel. There’s also the occasional “security enthusiast” consumer.
In addition to two exposition halls filled with booth after booth of electronic security devices, services and software, there’s a full agenda of classes on a wide variety of subjects. Unlike Black Hat, DEF CON, Toorcon, or HOPE, the RSA Conference is decidedly commerce-oriented, as opposed to research-oriented.

This past week, I attended the event in order to obtain more information about a couple of day-job related solutions to internal issues. However, I also kept my eyes peeled for things appealing to the average ITS reader.
Drone Detection (and Destruction)
![]()
Dedrone is a company offering the ability to detect drones, via a combination of hardware (RF Sensor 2.5) and software (DroneTracker). As the vast majority of commercially available drones are controlled by radio frequency transmissions, Dedrone has been actively profiling each drone’s specific frequencies and communications protocols. This allows their equipment to not only locate a given drone, but identify it as a particular type.
![]()
With a range of about 1km, Dedrone’s solution can not only detect drones, but also control their systems. This provides the ability to occasionally detect a drone before it’s even launched. DroneTracker also has a number of counter-measure options, providing the ability to define and enforce GeoFenced “no-fly zones.” This allows them to “catch” and control a hostile drone and jam or spoof radio connections between the drone and the pilot; as well as other means of disrupting or even destroying a hostile drone.
The company also offers additional equipment that integrates with the DroneTracker system, like a Modular UAV Jamming System. This allows the operator to disrupt communications with drones using GPS, GLONASS, Galileo, 2.4GHz WiFi and other communications spectrums. They also offer a DroneTracker Multi-Sensor, intended for permanent use in an installation like a prison, nuclear power plant, embassy or other high security location.
For non-permanent installations, they’ve created an “Event Kit” geared towards temporary deployment of a DroneTracker system. This is for one-time events like sporting events, state visits or other non-permanent installation situations. Finally, they make a Drone Detection Radar unit, which can basically augment the RF monitoring already provided by a DroneTracker system.
Hardware-Encrypted Hard Drives

Poway, California-based Apricorn has been making external USB hard drives with hardware-based encryption for a number of years now and they had their wide array of products on display at the conference. Some of their new advancements included extremely speedy USB 3.0 drives, fast enough to be used as boot drives and a “Configurator,” allowing for automated configuration of multiple drives in an enterprise environment.
This would allow admins to setup company-wide security policies on a bevy of Apricorn drives simultaneously through a software interface, rather than losing hours with manual configuration on a drive-by-drive basis.

Over the years, Apricorn encrypted drive capacity has grown quite a bit. Flash keys, portable hard disks, portable solid state drives and desktop hard drives run the gamut from 4GB to 10TB.
In fact, the Aegis Padlock DT incarnation even offers FIPS compliance (Federal Information Processing Standard 140-2, a US Government computer security standard).
Two-Factor Authentication Devices

Yubico is a company that, among other things, makes USB security keys which can be used in conjunction with your username and password/passphrase in order to authenticate your identity. A configured YubiKey can be used to authenticate user login to Windows, Mac OS and Linux systems. It can also be used with a slew of different internet services that allow you to set up a “security key” as a method of two-factor authentication.

Often, people will use their mobile phone as a 2FA authentication device; Dropbox, Gmail, Facebook and more are all more than happy to gather your phone number and send you an SMS to authenticate your login on whatever device you’re logging in from. Instead, setting up a YubiKey for this purpose allows you to keep your phone number to yourself and store your YubiKey on the keychain where you keep your house, car and other keys.
YubiKeys come in a variety of form factors, most in USB-A , though they’ve released a USB-C version (the YubiKey 4C). There’s also an NFC (near field communications) YubiKey (the NEO model), intended for mobile use. Configuration is dead simple; you plug the device into your USB port, visit the associated Yubico web portal specified on the packaging your key came in, follow the instructions and you’re done.
Secured Key Management
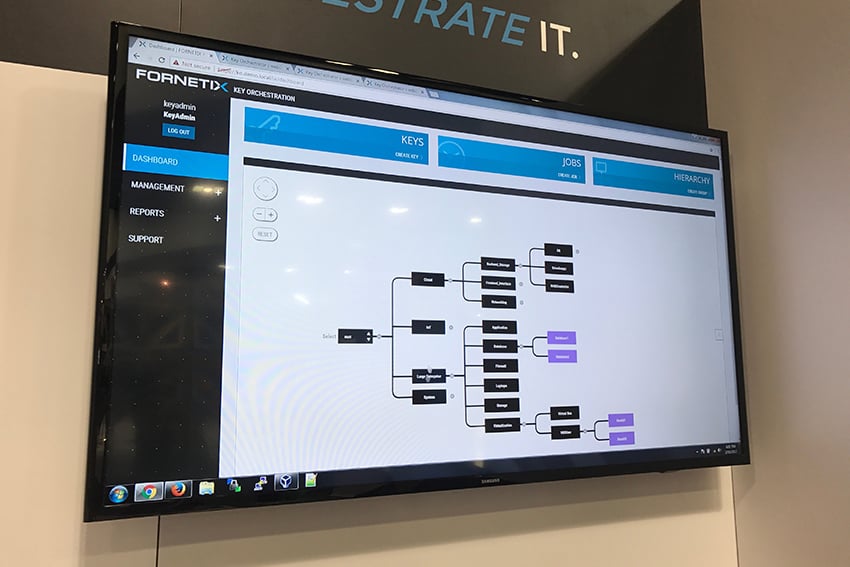
Anyone who’s ever had to deal with managing keys for encryption has likely lost a lot of time and probably even the occasional key. Something that seems as basic as generating and installing a certificate for a web server, usually ends up taking quite a bit of time with multiple steps in the process. If you get any of them wrong, you may have to start the process all over again.

Fornetix has built a system to manage those certificates, SSH keys or any other cryptographic software keys you use in a network environment. This is all done from a secured appliance (meaning the hardware is hardened to Federal standards), allowing you to distribute those keys or certificates to whatever devices need them, with the ability to create organizational and device hierarchy that fits your organization.
We went through a demonstration in which they generated new x.509 certificates for three web servers, then installed those certificates and automatically restarted apache instances on all three web servers. It was done, end-to-end, in a little under four seconds.

An example implementation of their system, as described by CTO Chuck White, was as a solution to overcome the complexity and time it takes to re-key satellite networks in military use cases.
Without Key Orchestration, the process of doing this could take somewhere between days, to a couple of weeks. In a conflict environment, it may even have to be done manually while under fire.
With Key Orchestration, the same task can be done from the Fornetix appliance and propagated over the air to endpoint radios, in just a few minutes.
Currently, a substantial portion of the Fornetix customer base is comprised of the intelligence community and defense agencies, though the benefits of such a system should be fairly obvious for large corporations managing large numbers of secure services.
Changing Threats and A Rapidly-Developing Industry

While the bulk of what’s shown at the RSA Conference is targeted at enterprise-scale security customers, it remains an interesting indicator of what may come down the pipeline to the end user. It also allows a glimpse into some cutting edge developments in the information security world, as they try to solve a constantly evolving series of threats from malware, ransomware, identity theft and the “Internet of Things” botnets, working in concert to destroy the fabric of the Internet as a whole through distributed denial of service attacks.
Every day, new threats are popping up in the security world and it’s great to attend things like RSA, which highlight people working on the opposite end to ensure there are protections against them. I’ve only briefly touched on a few products at the conference and if things like this are of interest to you, I highly recommend you see them in person if you’re able to attend next year’s RSA Conference.
Editor-in-Chief’s Note: Matthew Sharp is a Plank Owner and Life Member at ITS and goes by the username “viator.” He lives in The People’s Republic of Northern California and enjoys long range shooting, carrying heavy objects great distances and fuzzy little puppies.











Discussion