Inside Red Team Operations, Part 1: Planning, Recon and Equipment
Inside Red Team Operations, Part 1: Planning, Recon and Equipment
- Inside Red Team Operations, Part 1: Planning, Recon and Equipment
- Inside Red Team Operations, Part 2: Analyzing Recon Data and The Dry Run
- Inside Red Team Operations, Part 3: Execute, Execute, Execute!
 In this three part series we’re going to go through what it takes to perform a security vulnerability assessment that would ultimately end in the penetration of the target.
In this three part series we’re going to go through what it takes to perform a security vulnerability assessment that would ultimately end in the penetration of the target.
In part 1 we’ll talk about planning the operation, digital & physical recon and some of the kit we might need. In part 2, we’ll analyze the information gathered during the recon, plan and rehearse the operation and perform a dry run. This will test what we’ve learned and polish our plan. In part 3 we’ll execute the operation and plan for contingencies when things don’t go as planned.
What is a Red Team?
In the world of computer and information security, a red team is a group of highly skilled experts hired to provide adversarial services, i.e. to act like attackers. The goal of red team operations is to continuously challenge the plans, defensive measures and concepts of the organization.
These exercises result in a better understanding of possible adversaries and help to improve counter measures against future threats. Red teams are also tasked with probing physical security measures, sometimes as part of an overall digital/physical assessment and sometimes as a project of its own.
This series will focus on a combination of both physical and digital vulnerability assessments, as well as penetration of the target. This way you can see the techniques needed for both.
It is important to mention that each project/operation is different and the techniques described here will have to be adapted, changed or completely dropped based on the target. It is also important to mention that I will keep the technical details to a minimum. I’m doing this for two reasons; one, because not everyone reading this has a background in computers and two, because I don’t want to show the bad guys any technique they can use.
With all this in mind, let’s begin.
The Project
We’re tasked with penetrating the internal network of a fortune 100 company. If successful, we are also tasked with acquiring highly sensitive marketing documents.
There are many ways to try to penetrate their network and systems but we are going to focus on two. We will try a purely digital approach first, if it fails, we’ll try a physical approach that might give us a way into their network.
The digital approach usually entails scanning their public facing systems in search for a vulnerability to exploit, or a more direct approach that includes social engineering (hacking people into providing information) and a well placed weaponized document or attack code. A physical approach is just that. Physically penetrating the premises, trying to either get to a computer inside or connecting your laptop to their network and trying to find the documents. More often there’s a backdoor to access the network remotely from the convenience of your office/TOC.
Planning and Initial Recon
The initial recon and planning phase is critical. Some operations fail because of lack of information about the target, others are highly successful because the recon was carefully performed and all the possible weak points were identified.
Digital Recon
Let’s start with information in the public domain. Open source intelligence (OSINT) gathering is our first priority. You’d be surprised how much information about companies, their employees and the technology they use in their networks is really out there.
We can start using Google, Yahoo, DuckDuckGo and other search engines, however it would be good to use a search engine aggregator that can search across all search engines at once. It’s also useful sometimes to use the local search engines if we’re targeting a company or organization in another country.
There are services that provide a list of local search engines, or you can try local Google or Yahoo versions. For example, for russia try google.ru and ru.yahoo.com, for Argentina google.com.ar or for France google.fr. You get the picture.
We begin by searching for the company’s web sites, domains, press releases that might indicate the use of a certain technology, names of employees, high level executives, etc.
Press releases are a great resource, for example, they usually detail new products with names of technology, executives and other snippets of information that we can use for a social engineering approach.
Next we search for emails. We can type “@companydomain” and usually you’ll get a list of sites where people used their company email address for various tasks. This is a great source of information about employees (possible targets for social engineering) but more importantly, a lot of times IT people go to technical forums to request help about the technology they are using. It’s a great way to start mapping their operating systems, web servers, databases, firewalls, routers, etc. without having started the mapping part of the recon.
OSINT will usually take a few weeks. We want to gather as much information as we can and built a logical map of what we now know: people, systems, products and connections between all these.
Another great way to gather information is to call the company phone number off hours and if you get a voice mail probe for default passwords. Chances are you’ll get several hits. You can get a lot of good intel via this method. Getting the company’s different phone numbers is relatively easy.
The next phase of the digital recon is mapping the public facing digital assets. We want to know their digital footprint: IP address ranges, domains, websites and security devices if possible. This should be done very carefully, we don’t want to tip their security devices that we are mapping them.
We start searching the different “whois” databases for their different IP ranges. Since our target is a fortune 100 organization, chances are they have acquired a set of IP addresses that is static to that company. Knowing the IP ranges will allow us to also map those servers that might be connected to the internet but do not necessarily provide services (like a company website or e-commerce site do). You would be amazed at what you can find sometimes. In one project I found a server that had a Telnet service up and running, needless to say it was my way in. A developer enabled this for a project and forgot to disable it later. Humans… They are always the weakest link.
We want to map the ports open, the services behind those ports, operating systems, web server software, database software, versions of the software, email servers, file transfer services, etc. Once we have this information we can perform a very simple and fast vulnerability assessment and see what is exploitable right then and there. Sometimes this is all it takes, but most of the time it’s more complicated than this.
There are countless tools to do this, some open source, some commercial. Check online for more information.
Physical Recon
Now for the physical part. If we’re considering the possibility of a physical penetration we need to recon the target.
I usually divide the recon into two different methods: covert and overt. In a covert recon you’re usually either away from the target, using binos or scopes to surveil the target, or you are performing recon at night completely hidden. An overt recon usually means walking into the target’s premisses and pretending to be someone you’re not, while trying to collect as much information as you can by either observing or taking to people (social engineering).
During a physical recon I would also perform a scan of the premisses for any wireless, bluetooth or other RF that I can find. Many times during projects I found open wireless access points and routers. I logged right into them and used them as a channel in. As part of the kit, it’s useful to not only have a lightweight laptop during a physical recon, but also a wireless signal finder/scanner, wifi antenna booster, a good set of stumblers and other software to map all the signals you might find.
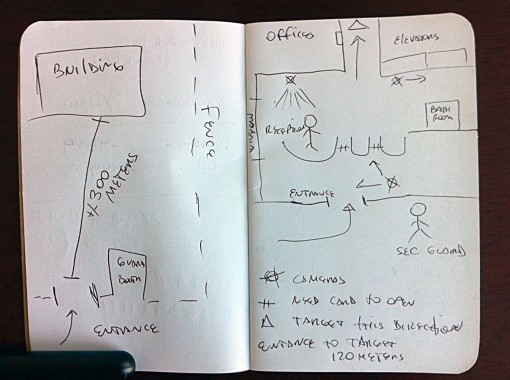
I found it very useful to perform a physical recon with a team of 2 or 3 members. You can send one around the premises to check any possible ways in (in case we need a covert entry), while the others maintain a tight surveillance. Key items to map are dress code of employees, badges or IDs they have, working hours, guards and their schedule, different access points to the building, daily activities (day & night) and also paying attention to trash collection, product delivery, etc.
Equipment
A good camera, scopes and other observation gear is needed here. Usually hunting stores have great gear you can get. All this will provide a clear picture of what’s going on around the building, but not inside. Like I mentioned, sometimes you have to perform an overt recon.
For these, I find it very useful to have a small voice recorder and have it on as soon as you walk in. It will record any information people might give you, while also recording atmospherics: a loudspeaker announcing company news or the name of an employee, normal working noise, etc.
Also carry a USB or a small wireless card with you, sometimes during the recon you’ll find yourself in the position of having a brief access to a computer inside the company. Plug that wireless router/card (pre-configured to a certain name/password) and try connecting to it later when you leave. Carry a set of lock picking tools, I like the Bogota Entry Toolset. It’s small, easy to conceal and in most cases work like a charm.
Also, I like to carry a small LED light, which is useful to check inside server racks and other tight spots, a small knife, a pen and a notepad.
Pen and paper might seem a bit outdated but it’s a great way to create a sketch of the site: doors, elevators, access points, guard and camera locations, etc. It’s is an invaluable tool for a physical recon.
Summary
We’ve just gone through the initial information gathering and recon phase. This is a critical phase and can make or break our operation.
You need knowledge to perform the technical part, but overall you have to be creative. Think outside the box, think like an attacker, try to figure out what they would do to gather information. For example, large corporations usually have a cafeteria or restaurant inside their building. This is a weak spot during lunch time, with a lot of activity. You could sneak in dressed as a cook, or even a server and you’re inside.
Bend the rules.
Stay tuned for part 2 where we’ll talk about analyzing the data gathered during our recon, as well as the planning and execution of a dry run!











Discussion