Looking at Security through the Eyes of a Physical Security Analyst
Looking at Security through the Eyes of a Physical Security Analyst
While my background is mostly in computer security, I’ve always been interested in the intersection of physical security and the general concepts behind the field. Through this has come a number of physical security classes where I’ve honed skills like lock picking, bypassing, red teaming and social engineering.
Earlier this year, I had the opportunity to take the CORE Group’s “Covert Entry Concepts” class, taught by Rob Pingor and Deviant Ollam. The Covert Entry Concepts class was heavy with hands-on experience, identifying and subsequently defeating locks and methods of illegal restraint. So when invited to take the follow-up class, “Physical Security Analyst,” given at the CORE Group’s facilities in Ellicott City, Maryland, I jumped at the chance.
The “Physical Security Analyst” class is geared towards individuals who have an interest in performing analysis of physical security systems in residential, commercial or government facilities. It was less of a hands-on “here’s how to circumvent any number of locks” class, but rather a class that gives some valuable insight into what someone who might offer these services would do in performing said analysis. It also covered the underlying ideas of what it means to perform these services for paying clients.

Upon arrival in Maryland, the class attendees met at one of two team houses procured for us. We then moved to the classroom in a nondescript office park nearby for pizza and a viewing of the movie, Street Thief. The film was created with the appearance of a documentary, though it was actually fictional. In the movie, the filmmakers follow the exploits of Kaspar Karr, a career burglar living and operating throughout the Chicagoland area.
Karr discusses and demonstrates a number of physical entry and escape techniques, as well as the meticulous planning, reconnaissance and social engineering necessary to successfully ply his trade. As this class was aimed at people attempting to defend against people like Karr, it proved valuable to see what we’d be defending against.
After the movie was over, everyone headed back to their assigned team house and rested up for the next morning, which was to be our first full day of class. Upon re-convening Saturday morning at 0900, we began the deep dive into the material the class would cover.
What Are You Protecting?
One of the primary questions a physical security analyst has to determine is what they’re being asked to protect and its relationship between actual and perceived value. Keeping this in mind, there are different levels of security based on the actual value of what you’re defending.
Minimal
Minimal security includes the definition of borders or boundaries and hopes to deter opponents; preventing them from gaining access with simple locks and simple barriers.
Low
Low level security intends to impede and detect threats by means of employing reinforced doors, window bars, high security locks, simple security lighting and alarm systems.
Medium
Medium level security intends to impede, detect and assess external threats with advanced intrusion detection systems, establish a perimeter with penetration-resistant fences and can include unarmed security personnel.
High
High level security impedes, detects and defeats threats. It’s marked by the existence of formal response plans, close ties with Law Enforcement, high security lighting and physical access controls. These access controls include things like RFID badge readers, retina scanners, etc.
Maximum
Maximum level security’s goal is to impede, detect, assess and neutralize threats. It’s defined by everything in the previous levels of security, with the addition of sophisticated alarm systems and highly trained armed response units on site.
What Are You Defending Against?
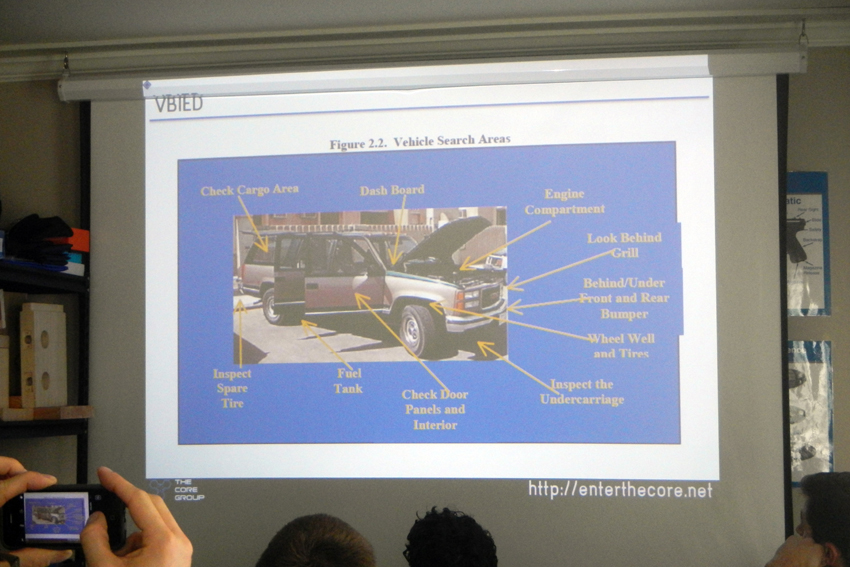
Another primary question in physical security analysis is who are you trying to guard against? There are various levels of threats, just like there are various levels of security.
Unskilled Threat
These are people with a small knowledge base, no support system, detailed planning or sophisticated equipment. An example of this would be people with no experience who attempt to commit a crime of perceived opportunity.
Street-Hardened or Semi-Skilled Threat
These people have a greater knowledge base and may be more aware of intrusion detection systems or the presence of guards. They may also have some limited technical or financial support.
Their conduct is distinguished by a higher level of detailed planning, some team coordination, use of specialized tools and attempts to cover their tracks. The fictional Mr. Karr from “Street Thief” is a solid example of the street-hardened or semi-skilled threat.
Professional and Skilled Adversaries
These threats have a great deal of training, engage in extensive pre-incident reconnaissance and make an effort to know everything they can about their target. They’ll also have extensive technical and financial support systems.
Their conduct includes thorough planning, attempts to defeat intrusion detection systems, capitalizing on vulnerabilities of the target security system and the practiced use of sophisticated tools and techniques. They may also have high-end access to “Tier 1” level tools and equipment. They’ll definitely use tightly coordinated group actions, with distributed skill-set specialties amongst the members of the group.
Hard Truths About Physical Security Analysis

In the class, we were warned the security analyst job isn’t an easy one and that very few people fully understand overall security, much less physical security. While physical security measures are always used to protect information, the reverse isn’t always true.
Upgrading physical security equipment costs time and money, which can be in short supply in a corporate or government environment. Security isn’t a profit center, it’s a cost center and is often looked at from a budgetary standpoint as unnecessary. That is at least, until the first time something goes wrong.
Once a breach happens, funds to address security concerns can suddenly appear. As a physical security analyst, it’s important not to take these things personally; your job is to assess and recommend courses of action. Once you’ve done this to the best of your ability, taking action to address these concerns is in the hands of those who control the purse strings.
You present a problem and suggest a solution. You’re often times working against a complacent institutional mindset that may want to save money by ignoring what you find or suggest. However, nothing loosens wallets like a critical incident.
Dilemma of Protection

Implementing increased security procedures, architecture, or policies, often times has to be balanced against aesthetic concerns or convenience. The reality is that you can’t defend against every threat and in a corporation or other organization, people need to be able to perform their duties. So simply adding more layers of security that slow them down from completing their work, gets in the way of the overall goals of the company or organization.
Aesthetic concerns are a factor as well; a technology company is unlikely to want to have their workplace environment looking and feeling like a maximum security penitentiary. Despite the fact that such an environment might provide greater degrees of protection of their intellectual property.
Also, the aesthetic environment has a legitimate effect on the productivity of those working within it. Proper security intends to find a functional balance between protecting that which an entity deems worthy of protection, while still maintaining a productive environment for those who work there.
Physical Barriers

Physical barriers are generally outer-layer security measures and include anything from perimeter fences or walls, to passive and active vehicular barriers, shrubbery and gates.
Fences
There are a wide variety of fences available, in various materials. The most common fences are chain-link, though “anti-climb” fences also exist. These make climbing more difficult by using a significantly tighter mesh than normal chain-link fences. There are also Anti-Terrorism/Force Protection fences, which are part of an overall ATFP federal security program. These are generally anti-climb fences with strengthened, reinforced cables run throughout the mesh of the fence.

Some fences are angled inward at a certain height, in order to make climbing more difficult, while other fences may have “toppers” such as barbed or razor wire coils interlaced and mounted to the top of the fence. Some are hybrids of ATFP fences, anti-climb fences, angled fences and fences with “toppers.” However, at best, fences predominantly define boundaries and keep animals out. While they can buy some time for a reacting security force, they won’t stop a dedicated attacker.
A prime example of fairly effective fence deployment can be seen at the facilities in Guantanamo Bay, where tall fences with “toppers” are alternated with patrol pathways and deep trenches. Without going into too much detail, the series of physical barriers in place at Guantanamo Bay may not completely stop a professional group of attackers. However, they will definitely buy significant time for the highly trained, armed response units that make up the next layer of security at that camp to arrive on the scene and address whatever threat may be there.
For most commercial installations, the accepted standard for fences is:
- At least 7 feet tall
- Utilize 11 gauge wire
- Constructed of 2” mesh
- Uses a 12” topper (razor wire or barbed wire coils)
Signs

Obviously, the primary function of signs is to convey information. In this context, signs can be used to good effect as a security measure, letting potential threats know they’re being watched, or indicating a facility’s security posture is an aggressive one.
At the same time, signs can also indicate to those threats that something of value resides inside. So the use of signs should be smart and shouldn’t inadvertently give potential threats too much information that can be used against the target.
Vehicle Barriers
A facility can employ the placement of either active or passive vehicle barriers in order to thwart vehicles from approaching too close to a target. Hydraulic bollards which can be raised or lowered can make it difficult, or even impossible for a vehicle to progress toward a target, as can static bollards, strategically placed.
Placement of both active and passive barriers needs to be fully thought out though. If a vehicle can simple go around these devices, they’ll fail to serve the purpose for which they’re designed.
Defensive Shrubbery
Some plants have natural characteristics that make movement through them difficult. Holly, roses, honey locust and raspberries all provide positive aesthetics, but will make egress through them painful, at best.
It’s also important to remember when using defensive shrubbery, that you’ll still want visibility. The goal isn’t to build a wall of plants, shrubbery should be lower than eye level. Trees should also be trimmed to above eye level. In addition, when planning plant use, you should consider the differences in time of day.
Pedestrian Gates
Pedestrian gate mechanisms can manage flow of people coming in or out and can help control access to a facility. They are, in essence, the beginning of your screening process in a layered security approach.
Defensive Lighting

Lighting used as a defensive technique should be continuous, fixed and stationary. In addition to ample coverage of open spaces between the outer perimeter and any buildings on the facility, entry lights should cover all entrances. Other aspects to consider are standby lights, portable lights and emergency lights. Depending on the situation, all of these can provide value.
There are a wide variety of light types, with different advantages and disadvantages. These include incandescent, fluorescent, mercury vapor, metal halide, high-pressure sodium and low-pressure sodium lights. All serve slightly different purposes across a spectrum of price points.
While in the past, fluorescent and high pressure sodium lights may have been the prime contenders, but these days they’re being replaced by light emitting diodes (LED), which are on average, roughly 25% brighter and use 85% less energy. They also have a significantly greater lifespan than other forms of lighting.
For placement, you’ll want to make sure you illuminate boundaries, avenues of approach, entryways and functional areas within the perimeter you’re trying to protect. Another aspect of lighting to consider is making sure you’re not impeding any camera system that may exist.
Rob told us that it’s a good idea, when evaluating lighting in a given area, to use a photographic light meter. Standing directly below a light, you can use the meter to take a reading. As you walk away from the light, the reading will lower. When the reading has reduced to 50% of the initial reading, you may want to look at placing another light there.
Drinking from the Firehose

In the remaining hours of the first full day of class, we went over guards and guard houses. There are a variety of factors to consider here, including wall construction, door construction, types of doors, door materials, ANSI testing, levels of doors and door locks. This led us to a little bit of in-depth discussion of locks in general, though not to the degree they were covered during the “Covert Entry Concepts” class.
We also touched on hotel safes and learned some interesting workarounds for most of them. We then moved onto external intrusion detection systems, including fence sensors, attenuators, ground sensors, microwave sensors and the like. We briefly touched on Sensitive Compartmented Information Facilities (SCIFs), which have become their own vertical cottage security industry post 9/11.
Finally, we did some preliminary OSINT (open-source intel) recon on the location that would be our field exercise the next day. After this, the two team houses broke off for dinner and prep for the next morning.
Field Exercise

I apologize in advance for being sparse with any identifying data on our contact or the location of the field exercise. As a matter of general principle and in consideration for both the facility and contact’s desire for privacy, I won’t mention the actual site we evaluated or mention our contact’s name. Furthermore, the photos for this article have been scrubbed of any identifying information and if for some reason, readers are able to recognize the location, please keep that information to yourself.
At around 0830, we all gathered at the facility we’d be evaluating that day and met with our contact. At this point, he briefed us on the changing demographics of the facility, surrounding neighborhood, history of the area, security policies and systems in place, recent security incidents and routine or nearly routine security incidents and most importantly, the concerns and security issues our contact felt needed to be addressed.
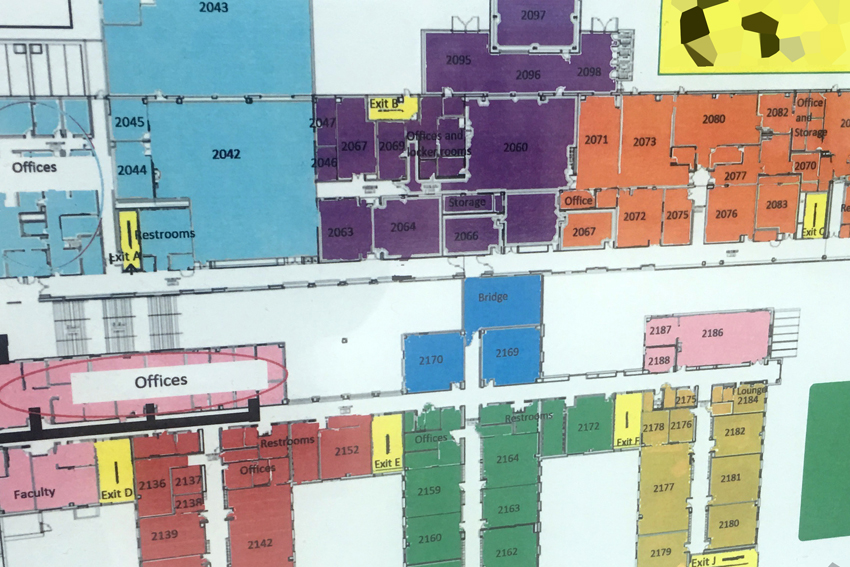
The focus of the entire class was to provide a framework for people interested in performing physical security analysis in a professional capacity. In addition to providing technical information, one lesson in particular was a crucial one; as a security analyst, your primary focus should be on solving the problem the facility personnel who contacted you has described as his or her main problem.
While you may notice a wide variety of vulnerabilities and even provide methods to resolve or mitigate these, if you fail to listen to the people who brought you in when they describe what they’re looking to get from your services, you’ll be failing to deliver what they want.
For our group, the problems our contact wanted our specific input on were the flow of individuals through the building at particular times and the evacuation policy for people in a particular area of the building, upon arrival outside. That is to say, getting everyone out of the building wasn’t a problem, but how to manage that area’s population once they were evacuated, given a rather geographically constricted area outside this part of the facility.

We took an extended tour of the outside of the facility and managed to find a number of concerns, including windows that had been left open and a door that had been left unlocked. However, we also found the surveillance camera system did a fairly good job of providing visibility of all areas surrounding the facility.
We then went through the inside of the facility and everyone took notes of what they found. Notes included doors that had enough gap to employ an under-door tool, security camera locations and the noticeable smell of natural gas in a kitchen area (a burner had been left on, but unlit).
We also found laptop storage cabinets that were unlocked, with keys readily accessible to anyone who happened to walk by them. However, our contact assured us that the theft of these items was a non-issue; the normal inhabitants of the building had yet to even attempt stealing any of the devices.

During our tour, we noticed a sensor in the open lobby area and we weren’t sure what it was for. It was about 40 feet up in the air and wasn’t near any entrances or exits. When we asked about it, we were told it was an earthquake sensor and that they inadvertently discovered an issue when flying a drone inside the building that broke the beam between the sensor and its partner at the other end of the area, triggering an attenuator.
We toured the main areas of the building and the controlled access areas, as well as the server room. The lock to the server room was found to be perfectly adequate, though access to the server equipment inside the room was insecure. (Cabinets weren’t locked or otherwise protected). However, this was a non-concern for our contact, as this particular facility didn’t retain any confidential data on the server equipment, nor was it a particularly attractive target for the normal inhabitants of the building.
When our tour and note-taking was complete, we met back at the classroom to cover the use and considerations of CCTV systems and microwave sensors. We also discussed the wisdom (or lack thereof) in using “fake” security cameras. They’re generally ok as an additional method in residential situations, but a bad idea in commercial environments. We also touched on access control systems, badging procedures and the problem of tailgating, as well as some aspects of active shooter precautions.
Tools of the Trade

For the class, we were also provided with an overall equipment list that would be required for performing the duties of a physical security analyst. This list included things like basic lock bypass tools, picks and jigglers, a photographic light meter, good camera and a rangefinder.
Behavioral Profiling

After this, the subject discussed turned to suspicious behaviors and how to profile them. Situational awareness, sensitivity to baseline behavior and anomalies from said baselines, critical thinking and rapid decision making are all key.
Knowing what’s normal for an environment is a prerequisite for being able to spot things outside that norm. The ability to recognize, as described by Gavin de Becker in his book Just 2 Seconds, the “moment of commitment” and the “moment of recognition” is also highly beneficial to predict a suspect’s future behavior.
When monitoring people in an environment, you can create “suspects” based on the behaviors they exhibit. Are they “inspectors” checking their environment for things no one else seems to be checking for? Are they “organizers” perpetually adjusting themselves or items in their control? Are they “sweaters” perspiring when no one else seems to be perspiring? Are they “fashionistas” dressed significantly better than those around them?
All of these things could be indicators that these people don’t belong and may have ulterior motives for being there. Giving suspects a distinct nickname based on that behavior makes it easier to keep track of them, particularly in environments where there may be multiple suspicious persons.
Wrapping Up
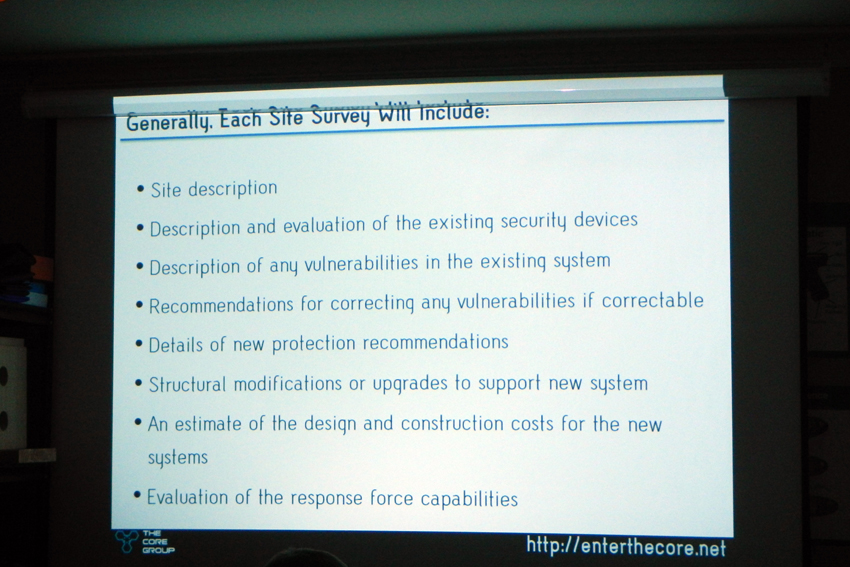
Once we finished up drinking from the firehose, Mr. Pingor gave us some business tips for doing this sort of work. A key tip was ensuring to include significant time for writing an extensive report when devising an estimate for a client. Another was not underestimating the value of your time and not being afraid to throw out what you might think is a “high number” to a prospective client.
After all, you’re providing them with your expertise, which cost you a certain amount of time and money to obtain. In the end. the worst they can do is say “no.”
The Takeaway Treasure Trove
At the beginning of the class, each student was given a binder containing examples of fairly comprehensive commercial and residential site surveys used by the CORE Group. While we didn’t explicitly cover the contents of the binder during the class, they were mostly self-explanatory, particularly when examined through the lens of having completed the class.
CORE Group offers a longer, more extensive version of this class through the SANS Institute, which goes into greater detail on each subject covered during this abbreviated version of the class. Still, provided you have some background knowledge on this subject already, this version of the class provides an exceptional value for the price. Not only for the wealth of knowledge imparted in such a short time, but also the binder full of CORE Group’s intellectual property (students were encouraged to use the material as we saw fit, but to not distribute it to the Internet as a whole).
Finally, what’s possibly the best value of all, is the networking you’ll get to do with the other like-minded individuals who take the class with you. While some of these faces were already familiar to me, I definitely got to spend more time with them individually, during which ideas got bounced and new connections got made.
Editor-in-Chief’s Note: Matthew Sharp is a Plank Owner and Life Member at ITS and goes by the username “viator.” He lives in The People’s Republic of Northern California and enjoys long range shooting, carrying heavy objects great distances and fuzzy little puppies.











Discussion