Infosec and Encryption to Protect Your Secrets
Infosec and Encryption to Protect Your Secrets
 Everybody has secrets and things worth protecting. It could be your family photos, your saved browser passwords, your bank records, or maybe just that totally legal MP3 collection.
Everybody has secrets and things worth protecting. It could be your family photos, your saved browser passwords, your bank records, or maybe just that totally legal MP3 collection.
Your laptops, thumb drives and even regular desktop computers all have a treasure trove of data that I’m sure you would not want an unscrupulous person to freely rummage around in.
You’re not alone. The military, rebels, banks and corporations have the same infosec concerns. While your information leaking may not cause a national security crisis, it’s a crisis to you. As a prepper, that means you do something about it now, and not when you come back from the coffee shop bathroom to find your computer gone.
Threat Assessment
Before we go any further, I wanted to take a second for a reality check. Crypto-geeks and some of us survivalists think our primary threat comes from NSA black helicopters coming to “disappear” us. There is something to the strategy that protecting your data from the government protects it from all other threats; there’s also something to the idea of building a nuclear bomb shelter to protect you from burglars.
First, it’s much easier for state and Federal agencies to just request your data stored on third party systems. All it takes is a signed warrant to force your email, cell phone carrier or social network provider to hand over every private message, IP address (which often leads to physical location), and login history. If you want an interesting read, the Electronic Frontier Foundation obtained a Department of Justice PowerPoint on how LEO’s obtain information from social networking sites.
Second, if SWAT does kick your door open and they seize everything in your house with a transistor, I suspect they have the means to access any data they want. If your state forensics analyst does not have the means, the FBI’s cyber crime unit certainly has access to the computing resources to break your keys within a matter of months (if not hours).
Third, some federal agencies maintain portfolios of security vulnerabilities to use in operations. It could be a hardware or software key logger, a browser vulnerability, or unpublished vulnerabilities in your encryption software. If they do not have the tools on-hand, they likely have the resources to buy them from the black market.
The entire process may add months or years to the investigation, but most any encryption system will be compromised by a sufficiently funded and technical attacker. Worst case, someone breaks your kneecaps and you hand over the keys. Fortunately, you and I will probably never deal with that. Our attackers will likely will be airport luggage thieves, strangers finding your thumb-drives, disgruntled co-workers, and at worst, professional data thieves such as corporate spies and private investigators.
File and System Encryption Overview
We need to use some specialized tools to lock down where the data sit. In today’s article, we’ll be focusing on file and system encryption software and in particular the TrueCrypt application. There are other tools to consider, such as data scrubbers and hardware encryption, but if properly deployed software encryption can be a near-complete solution for data at rest.
Encryption in general means manipulating information in such a way as it cannot be interpreted unless the reader knows a secret. It is nothing new, and has been practiced for centuries by military leaders and revolutionaries; the kama sutra even lists it as an “art” all wives should practice to better arrange secret meetings with lovers. Primitive encryption systems originally used the encryption method itself as the shared secret, but more sophisticated algorithms are publicly known, but take a secret password/key. In the computer age, this means storing the data on your hard-drive using an encryption key.
This does not protect you from someone seizing your data while your machine is running, or theoretically if it has been recently turned off five to fifteen minutes. Also, if you are just using file encryption or a file container and not full-disk encryption, your operating system is likely to store your open file temporarily in an unencrypted area that can be later retrieved.
What it does protect you against is someone stealing your device and accessing the data within. Even a simple operating system password, like a Windows login/screensaver password, is relatively trivial to break even for unsophisticated attackers. Only by encrypting the data on the hard disk platter can you protect it.
TrueCrypt
TrueCrypt is a free, cross-platform encryption system that can handle file, device, and full system encryption. While not open-source, the code is available for the public to review for vulnerabilities and backdoors. This is an important distinction between this system and some proprietary alternatives such as BitLocker, because you have the benefit of thousands of eyeballs looking for flaws, versus an internal quality-assurance team. Also, closed-source security systems have a nasty habit of building backdoors for admins and governments, which become a door for anyone at all.
There are supposedly two authors who remain anonymous; one can speculate about their motivations, but given its track record, I trust it more than black box encryption systems.
Virtual Drives and File Containers
TrueCrypt uses virtual drives to handle encrypted data “blocks”. When you access an encrypted file container or encrypted thumb-drive, it looks like another hard-drive inside your computer. In this example, I’ve loaded the file “SecretPlans” as my Z:\ drive; this means anything I add or edit on my Z-drive is actually inside that SecretPlans file on my desktop. This method allows any of your existing software and OS to interact with encrypted data without any modifications. Neat, huh?
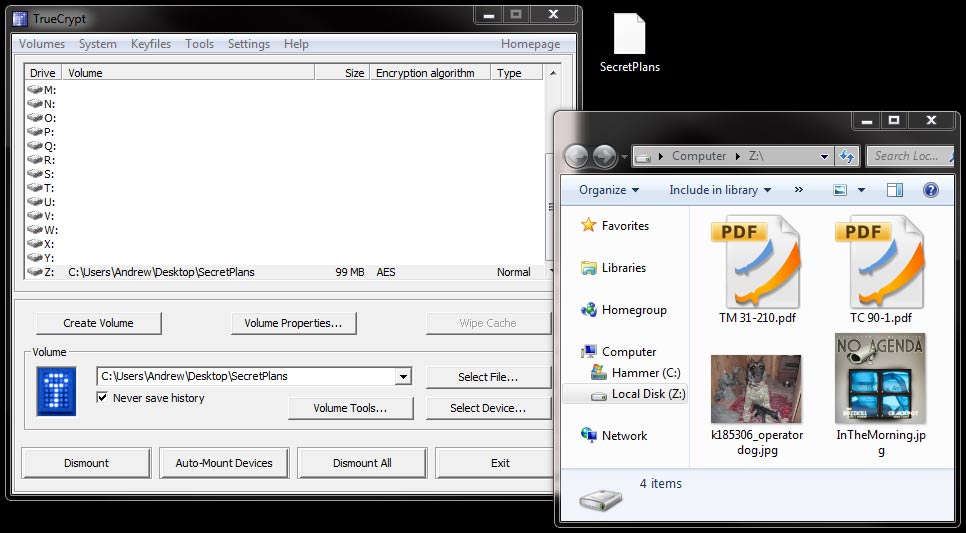
The example above uses TrueCrypts file containers. You can think of them as encrypted ZIP files or a virtual thumb-drive. Once created, they can safely be emailed or burned to a CD. To create one, just click “Create Volume” from the main window and follow the wizard. This isn’t an article on encryption methods, but suffice to say the AES encryption method is what the Department of Defense recommends for all material classified top secret.
Hidden Volumes
An interesting feature of TrueCrypt that you can build a secondary password into encrypted containers and devices for decoy data. By selecting “Hidden TrueCrypt Volume” during the creation wizard, you can set two passwords for the same thumb drive or file container. In the event you’re forced to reveal a password (through the use of rubber-hose cryptoanalysis or you’re re-entering the country) with one password you reveal your actual data, with the second, you reveal some sensitive but unimportant data (such as old credit card statements). Theoretically, because the encrypted data appears statistically random, it’s impossible to determine if there is a secondary encrypted volume present.
Full Disk Encryption
Most of the other encryption methods are useful for a limited set of cases (transmitting containers, carrying them on the thumb drives, etc.), but do leave bread-crumbs on the machine that can be recovered through forensics means. Also, your browsing history, your downloaded email, and other moderately sensitive data probably shouldn’t be in the hands of data thieves. The only sure way to protect these data is to encrypt the entire hard-drive, operating system and all.
TrueCrypt makes this dead simple. After you have a CD burner and a blank CD handy, inside of TrueCrypt type “System” and then “Encrypted System Partition/Drive”. The wizard does a good job walking you through, but it does force you to burn a rescue CD in case it becomes corrupted for some reason. The encryption process can take up to a day, but you can use the system normally and even turn it off. After it has finished encrypting, before Windows comes up on the boot process it prompts you for your password. If you try and access the hard-drive from a bootable CD or with an external enclosure, it’s mostly impossible without a password. Follow the advice for using strong passwords and most any data thieves will be left empty-handed. Even if it means writing it down and keeping it safe, it is better than using an easily cracked password.
Limitations
Fill disk encryption is not a panacea. It is a tool in your larger information security strategy, like the locks on your door or your carry weapon. Here are some things it does not protect against.
- Data in motion. Data being transmitting over a network or by thumb drive are leaving your encrypted bastion, and can’t be protected.
- While the machine is running. Your data are unencrypted while the machine is running, so if someone gets access via malware or seizure it is not going to do a lick of good.
- If your backups are unencrypted. Your external hard drive and your DVDs that hold your backups need to be encrypted to, otherwise you left your back door open.
- If a skilled data thief is prepared to capture RAM data if the machine is recently turned off.
Conclusion
Infosec, like any other operation, requires considering attacks from all sides, mitigating the risks, and using the right tools. While it’s not taking on the nuclear wasteland with your AR and a case of jerky, as a prepper you understand threats come from all places. If you want to protect yourself against a PI your ex-wife hired or a curious, power-hungry TSA agent, then consider encrypting your devices and system.











Discussion