Red Teaming and the Adversarial Mindset: Have a Plan, Backup Plan and Escape Plan
Red Teaming and the Adversarial Mindset: Have a Plan, Backup Plan and Escape Plan

Recently, I attended a fascinating class given in San Francisco by fellow ITS Tactical contributor and author of the Red Teams Blog, Uri Fridman. The class, “Red Teaming and the Adversarial Mindset,” was a solid overview of what Red Teaming is and how it works. In addition, it covered how the practices and thought processes used by a successful “red team,” can also benefit an individual when applied to the decision making processes we all face every day.
The class was held over two days, featuring a fair amount of classroom instruction, some group exercises and ultimately, a field exercise, in which the various students were divided into 3-4 person small teams and given a goal to achieve using the techniques and mindset we had been taught.

What is a Red Team?
We started at 0900 on Saturday and immediately dove into what a “red team” is, what it does and why it exists. A red team is an organization tasked with the duty of becoming a “thinking enemy” in order to test the physical, digital and social aspects of a client or parent organization’s security. The red team must think and act as an adversary in order to properly assess the weak links in security.
A successful red team will not simply run through a checklist of things to test; they will perform reconnaissance, then dedicate themselves to figuring out a way to get past security measures that have been put in place. Just as an adversary would, they will try any and all vectors of attack; staying motivated like said adversary.
They will not play by any set of rules and they must adapt as the situation dictates in order to achieve their goal. They will test the security posture of an organization’s physical security, their digital security (don’t call it “cyber” security, lest ye be hit in the head with a bottle!) and their social security measures. If successful, the red team will present a report on their findings, pointing out by order of priority, what they found to be crucial, essential or desirable improvements that can be made to the hiring or parent organization’s security posture.

Ideally, they’ll work with the necessary people within the target organization in order to implement the changes suggested. For a great deal more detail on exactly what this entire process is, I highly suggest reading Mr. Fridman’s part 1, part 2, and part 3 articles here at ITS Tactical. All of that information and more was covered during our class and you’ll get more out of it by reading it directly from the source than you will from reading my recapitulation of the material.
The students in our class were a fairly even blend between people immersed in digital security (seriously; don’t call it “cyber”!) vs. people immersed in physical security. For this reason, I would imagine it was a bit of a challenge not to spend too much time on one side or the other and I feel Mr. Fridman did a good job of covering both, as well as addressing additional questions my fellow students had both during class and after.
Students ranged from security software or mobile/web developers, physical security professionals, risk assessment professionals, self-described ‘hackers,’ small business owners and even some prior or current law enforcement people. All of them were there to gain more knowledge on how they could implement red team tactics in their day to day work.
Three Aspects of Red Teaming
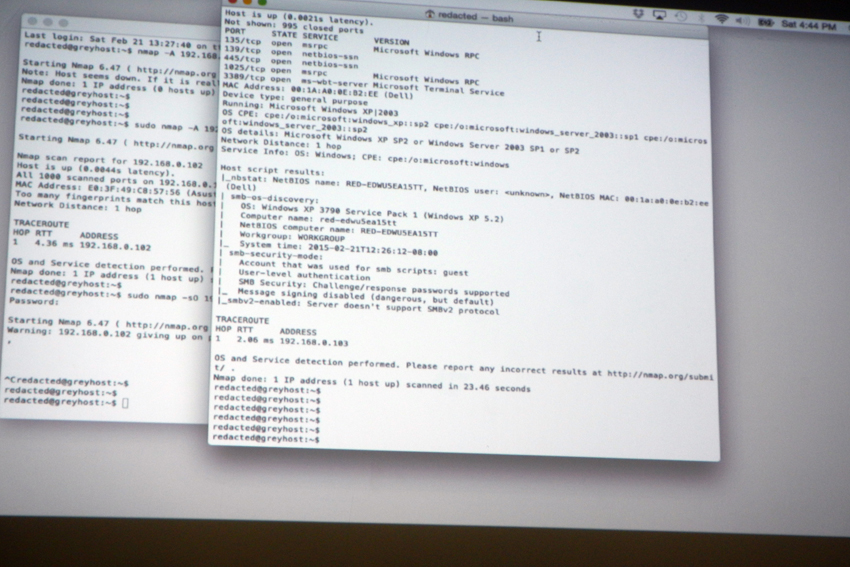
We covered the three primary aspects of red teaming and the first was the digital aspect. This is the use of reconnaissance to determine holes in electronic security measures, the use of OSINT (Open Source Intelligence) to gather all sorts of information about the target and potential vulnerabilities they may have, as well as valuable information about the organization’s employees that can be used in the third aspect, “social engineering.”
There’s also the importance of doing a dry run attack, which can be as simple as setting up a lab environment that matches the target’s infrastructure and then attacking it to insure the attack will be successful, followed by a live run, which is to say the actual attack. Then there is the importance of knowing what to do post-breach after the attack is completed. Once you’ve achieved your objective, you’ll have to know what to do once you’re inside their network (are you tasked with obtaining corporate information? Are you tasked with disrupting their operations?
What you do will largely depend on what you’ve been asked to test), followed by exfiltration (if you’ve found proprietary data, how are you going to get it out of their network and back to your local device?) and clean-up, such that you leave no trace of having been there, much the same way an actual adversary would do.

Physical Red Teaming
The second aspect is the physical aspect, which consists of recon that can mean staking a location out for days at a time, noticing who comes and goes and in what frequency they do so. It also includes checking for security cameras, fences, doors, types of locks, windows that might be usable in a physical breach, security personnel present at the site and their habits and schedules.
A red team will watch and gather data before moving to the planning stage, wherein that data allows them to see possible angles of attack that are uncovered by copious recon data. Once the data is collected and a plan is made, the breach can be executed with equal importance put on the follow-up to a successful physical breach; exfiltration. Your plan to get in is no good if you cannot manage to get back out, much the same way making it to the top of Mount Everest is no good if you can’t get back down the mountain.
Important points to consider when doing your physical recon are looking for high ground from which to observe, exploring the surroundings of the target, behavioral monitoring and an ability to develop patterns from that monitoring. Also, always relying on the man on the ground. No matter what your digital recon told you, if someone in the field tells you it’s different than that, it’s different than that.

Social Red Teaming
The third aspect is the social aspect, which means gathering information about the employees of your target. This includes their personal habits, email addresses, hobbies, schedules and anything else that might prove useful. If you’re going to try to get into a place using social engineering, it helps to know the corporate culture and local atmospherics of a place so that when you call and pretend to be another employee or vendor, you can speak the language they speak and use terms that will sound “right” to them.
In any environment consisting of digital, electronic and human security measures, the weakest link is most likely the people. With the human propensity to share information about their lives via social media, combined with OSINT tools, it isn’t tremendously difficult to find a way into an organization through a personal connection established by successful social engineering.
First you must observe the target, learning about it as much you can, then connect the data you have and track the target. Tools like Recorded Future, Paterva, Pipl, Spokeo, NetGlub, Google, iSeek, Shodan, Addictomatic, LinkedIn, Monster, Career Builder, Pastebin, reddit, Facebook and Twitter make this all the easier.
The important take-away from covering these three aspects was that while attacking one aspect may possibly grant you success, attacking all three will almost definitely grant you success. It is also important to be able to sift through the data you’re able to collect about a target, since the pile of information can quickly become overwhelming. Efficient organization skills, an ability to remain focused on your overall goal and proper planning are key.
Have a plan, and red team that plan.
Once you or your team have developed a plan to achieve your goal, it’s necessary to go over your plan and look at it for weaknesses, or points that you may have initially missed. It can also be quite helpful to have a fresh set of eyes take a look at the plan you’ve developed, as they may notice something you’ve missed. Whether small or large, addressing these will help make you plan more effective.
This was referred to as the “tenth man rule”; if nine people completely agree that a strategy or plan is correct, then the tenth person should take a contrarian view to avoid the pitfalls of groupthink, where fatal flaws in a strategy are missed in favor of group agreement. This philosophy is one where the value of red teaming extends far beyond the goals of a red team in this security context. If, in life, you’re deciding whether to move to a new place, take a new career path, or make some other major decision, first come up with a plan based on your observations and intelligence gathering.
However, before you act on that information, have an outsider examine your plans. They’ll likely find something you missed and encompassing that knowledge will only strengthen your final plan. Gather their impressions and adapt your plan if you need to in order to address the concerns they brought to your attention.
The first day of the class was predominantly classroom instruction, with some group exercises where we’d be given a physical layout and basic information about a building, which included a target inside that building. We were then told to come up with a plan to achieve the goal, whether it be to find out what was in a particular room inside the structure, or simply to figure out how to gain access to an area in the structure.
One team would present their plan and then the other team would offer their analysis of the plan they just heard, before presenting their own plan. The first team would then offer their analysis of the second team’s plan and a revision period would be granted in order for each team to consider the points made by the other team and address them in the form of a revised plan. The net gain of the “tenth man” were immediately apparent; both teams would end up with stronger plans, whether the task was to breach a building or to defend a building.
On the second day of the class, we went over the notion of “red teaming the plans” again in greater detail to learn the value of identifying risks, threats and vulnerabilities, then assigning relative importance or likelihood of them occurring in a written chart. This allows a team to prioritize what needs to be addressed in order to be successful. We also learned that equipment failure is almost always a top threat, with a very high likelihood of occurrence. The way to mitigate equipment failure is simple; apply the “two is one, one is none” philosophy and bring redundant equipment. As is the rule in life, this includes always having extra batteries.
Murphy’s Law applies to red teaming as it does the rest of life; if something can go wrong, it will go wrong. Plan on it going wrong and you’re one step ahead of the law. Have a plan, have a backup plan and have an escape plan. Simple rules can save the day.

Small Team Tactics
The next thing we covered were “small team tactics.” There are major advantages to working in small teams, which is something that the world’s Special Operations Forces have known for a long time; a small team is more agile, able to move faster and adapt more easily to changing conditions on the ground. A small team must know each other’s strengths and weaknesses. They must also know how their fellow team members operate under stressful conditions. They must plan accordingly.
Small team members also benefit from sharing knowledge with each other, effectively cross-training one another in their various areas of expertise. A small team may lack the resources of a larger entity, so they must keep the mindset of maintaining as much simplicity as possible. A plan with a large number of moving parts is hard to change if one or more of those parts turns out not to be working. A simpler plan is much easier to adjust if you need to adjust it. Most importantly, a small team must trust one another and include everyone in the planning stage to develop the best possible plan before acting.

Field Exercise: Infiltrate the Office
After the classroom instruction portion was complete, we were divided into small 3-4 person teams. Our task was to find out what was inside an office location. How we would achieve this would be up to each individual team. Mr. Fridman took us all outside and gave us a quick primer on various things to look for; open windows, security cameras, doors (are they locked? Might they provide access to the building we thought the office might be in?), scanning for wireless networks and using that information to determine where the office might be. We then all returned to the classroom to discuss with our small teams what our plan would initially be and set off to implement said plans.
The team I was on was a three person team and since I didn’t get specific permission to name them in this article, I will refer to my teammates as “R” and “T”. We decided to do some initial reconnaissance and did a walk-around of the overall building to try and get a feel for where the office might be specifically, as well as gathering potential physical entry vectors.

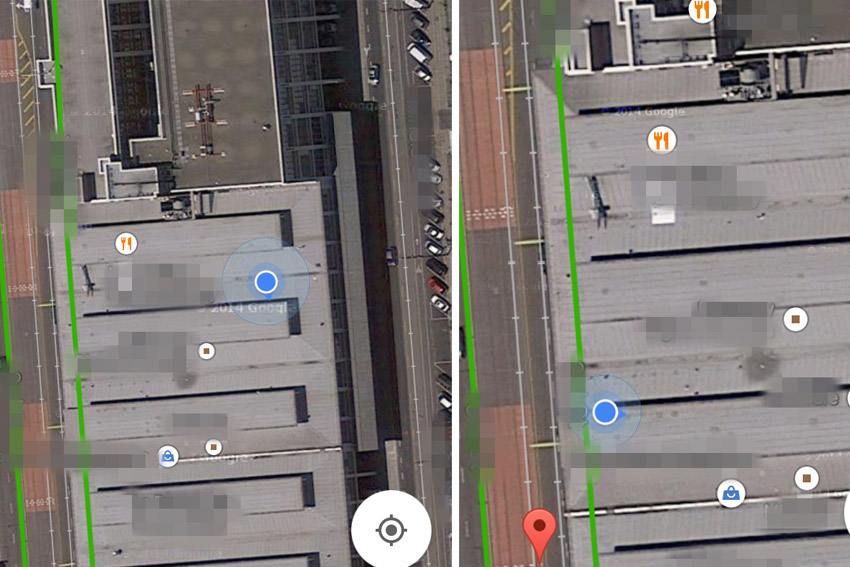
We knew from initial OSINT research that the target maintained an address on the side of the building used for shipping and receiving so we walked past there, checking doors to see if they were locked as discretely as possible. We also noticed a Wi-Fi network when we got to that door that, while secured and named somewhat obscurely, was most likely the office Wi-Fi network. R found a door propped open by a folded cardboard box a few doors down from the known address and was able to gain entry there and explore a bit.

We also rounded the block, noting a couple of prime locations for extended recon, including a grassy hill in the lot behind the building and an abandoned bank building on an adjacent corner. We took copious notes as to the presence of security cameras as we walked around to the front of the building. We also had a pleasant chat with a woman who apparently worked in one of the offices in the building, when she noticed we were trying to get buzzed into the building’s leasing office.
Being friendly with her and giving her the cover story that we were just interested in checking out office space in the building was enough for her to tell us that generally you had to call someone to buzz you into the building. She also told us that there was a tenant directory a couple of doors down from where we were. We gave her no reason to suspect we were trying to breach the building’s security and in fact, helped her out while she was juggling a couple of hot coffees. This showed a pretty effective tactic for social engineering; if you’re friendly with people and ask them for information, they’ll probably help you out.

Combined with what she told us, we found ourselves on the front side of the building at the same location we’d been when we were checking the Wi-Fi signal strength and saw what we were pretty sure was the address of the company offices. We were able to look through a window and see a directory of tenants in that section of the building which this confirmed we were in the right place. The door to that entryway was of course locked, but that would be a problem for after lunch. We returned to the classroom and gave the instructor our SITREP, then proceeded to scarf down pizza while drawing up our plans.

After lunch, we divided up; R and T would try to gain entry through the door propped open by the cardboard box and I would move my car from where I had previously parked to a spot across the street. I intended to use a camcorder with 700x zoom to try and see what I could inside where we thought the office might be. Additionally, I’d keep an eye out for counter-surveillance that might indicate we had been spotted (part of the overall goal was to avoid being caught by the designated security guards in the exercise).

Meanwhile, my teammates found that the door previously propped open was no longer propped open. They came up with an alternate approach of going to the company directory, selecting a yoga studio and buzzing them, claiming they were interested in checking out the yoga studio and possibly signing up for some classes. It’s probably for the best that the intercom system didn’t have a video component, as the ruse would likely have fallen apart if they’d seen my teammates, but it didn’t and the ruse worked.
T and R gained entry to the building and proceeded to explore the hallways and stairwells until they were blocked by locked doors. Back in the surveillance vehicle I spotted what I will refer to as Team Blue Falcon, for reasons I’ll get into later, sitting pretty conspicuously outside where we’d ID’d the front door, using their laptops to do whatever digital scanning they were doing. They stood out like a sore thumb from my perspective, but no security guards passed by and the regular citizens that did pass them didn’t seem too concerned. Then again, San Francisco is a pretty conflict-averse place so most people won’t do or say anything even if they think something is fishy.

Having been met with the locked doors, T returned to give a SITREP to Uri and R managed to find another method of entry through another door. While I watched from across the street, I saw the front door of the office location open and out walked R, at which point Team Blue Falcon used the open front door to gain entry. Partial success! Our team reconnected back in the classroom and revised our plan. We now had a known path to get to the office, which we followed again, looking for a potential fire exit/back door that might provide us with access. We did some Wi-Fi scanning near the front door, doing our best to stay out of sight of the camera mounted above it and saw a couple of really strong networks, but neither were open. Since none of us had laptops on us at the time, we were unable to pursue the angle of cracking the Wi-Fi to try and see if there might be security cameras which would give us a peek inside.

We searched the entire perimeter of the known office location and the floor below it. We entered the building sections north and south of the office location and checked every fire exit we could, only stopping when we saw a sign indicating that the door to the fire exit was alarmed and was not to be opened. For this class, we didn’t think it would be a good idea to ignore that warning so we didn’t open the door. We would later learn that another team did and there was no alarm.
During a search in the Northern section of the floors above the office, we tried to find a safe way to get onto the roof and potentially get a look inside via the skylights the office had. No luck. We tried everything we could, finding things like the power switch to the office and the utility closet that would have allowed us to shut everything down if our assignment been to disrupt operations. We also found a variety of exits and entrances to the building and the surrounding sections of it. Finally, we ran out of time and had to return to the classroom.

After Action Review
Class having reconvened, we listened as teams presented evidence if they had succeeded and explained what they had done in order to succeed. Team Blue Falcon were the first presenters and they had succeeded by finding an open wireless access network, on which they found two wired security cameras both with default passwords. They used those default-password cameras to capture video of the interior of the building, but not before they also had changed the open wireless router’s password, thus making sure so no one else could use this to do what they had done.
This was not a competition and the wireless access point and wired cameras attached to it had been installed specifically to allow class students to use this vector, so changing it was a bit of a Blue Falcon move, to say the least, thus earning them the title of Team Blue Falcon. It was pointed out to them that, generally, that’s not a very “red team” thing to do, but I suppose you’ll have someone like that in any class like this. It was particularly amusing to me that they’d been unaware of how conspicuous they’d looked while outside the building with their laptops while being watched from a distance.

We presented our findings and were asked what we would do differently if tasked with this again. Our answer was to first bring more equipment; a laptop with some basic tools like nmap, wireshark and the like would have been beneficial. We also thought, given more time, adding a social engineering approach could be helpful. Failure in this case wasn’t bad, as it allowed us to see what we could do to be successful in future attempts and we learned, which is exactly what I had hoped to gain from the class.
Other teams had a wide variety of approaches. One team had done an excellent job of preliminary OSINT gathering and knew the exact location of the office the night before the class. One team managed to get someone out a window, who then made his way across the rooftop of the building in order to take a look inside through the skylights. One team managed to use an empty FedEx box to trick the guards into opening the door for him under the pretense of taking receipt of the package, though he was unable to get a photograph or video of the inside. After each team that presented their results finished, the other teams would offer feedback on things overlooked, or things caught. We all had learned from each other, as well as our instructor and the hands-on exercise was enlightening.

While I came away with a notebook full of information, there is still much to be learned from this class. That being said, I would take this exact same class again, as I’m sure I would gain even more information from it. I’ve read the Red Teams Blog for a while now and have enjoyed the articles Uri has written here at ITS. Hearing him speak brings a narrative to what I’ve read on the blog and ties a lot of the material together for me.
He makes a fantastic instructor in what, for me, is a fascinating subject. After the class had ended, a good portion of the class retired to the brewery/barbeque place across the street and continued to discuss the material over beer and meat. It was there I learned that Mr. Fridman will be releasing a book in the next few weeks, which covers a lot of the rules and axioms covered in the class, leaving ample space for notes on the behalf of the reader.

His suggestion is that one read the book, go over it a couple of times and then use the note-taking space to explore what each section means to them personally. I’m looking forward to seeing this book and I would encourage anyone who wants to know more about “Red Teaming” to watch his website and sign up for the next class he gives. I learned a ton in a very short amount of time and Mr. Fridman makes an excellent instructor. Whether you’re deep in the digital security field, an old hand in the physical security field, or just interested in a philosophy that will help you make effective, rational choices, there is much to be gained from considering “Red Team and the Adversarial Mindset.”
Editor-in-Chief’s Note: Matthew Sharp is a Plank Owner and Life Member at ITS and goes by the username “viator.” He lives in The People’s Republic of Northern California and enjoys long range shooting, carrying heavy objects great distances and fuzzy little puppies.











Discussion