The advent of the Internet, including web-based banking, shopping, and all things financial, have created a popular culture that is at least trivially informed about cryptography. Most of us know to look for https:// or a lock icon in our browser before engaging in a sensitive transaction.
The advent of the Internet, including web-based banking, shopping, and all things financial, have created a popular culture that is at least trivially informed about cryptography. Most of us know to look for https:// or a lock icon in our browser before engaging in a sensitive transaction.
One major disadvantage of cryptography is that an encrypted channel sticks out like a sore thumb to an experienced digital sleuth. Enter the world of steganography, the art of hiding messages in plain sight and the advances in covert communication channels.
Using Photographs
The most rudimentary and widely known definition of steganography is hiding textual messages inside of photographs. If you think about today’s digital cameras, it isn’t uncommon for the average photographer to have inexpensive access to a 10, 12, or even 14 megapixel camera. An iPhone 4 uses a 5.0 megapixel camera that yields a .jpg measuring 2592 x 1936.
What if every 31,363 pixels were replaced with the byte equivalent of a character? That would yield a message about the same length of an SMS message, 160 characters. How many people would be able to visually detect the degradation of the photograph if 160 pixels out of 5 million were changed?
1s and 0s
Consider this: a bit is either a 0 or a 1 in the digital realm. A collection of just 6 bits provides 64 different combinations–enough space to include the upper-case English alphabet, numerals 0 through 10, and 28 open spots for punctuation; including a comma, period, colon, space, and carriage return.
Now consider an innocuous twitter account, where the posting includes an extra space after the last period to represent a 1, and no space to represent a 0. Every six tweets can effectively be mapped to a character. Sure, message delivery is slow in this arbitrary example, but the point remains. Even tweets and Facebook posts can carry secret messages!
Steganography Applications
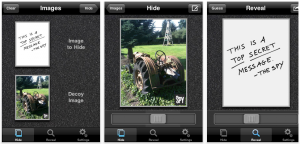 Both the iPhone and Android offer users low cost steganography applications. For example, Spy Pix and Hide It In are two applications that each allows the user to hide one photograph inside of another. Personally, I’m skeptical that a $0.99 app implements a sophisticated enough algorithm to remain undetected from a nation state, but it is probably good enough to fool a run-of-the-mill PI if used judiciously.
Both the iPhone and Android offer users low cost steganography applications. For example, Spy Pix and Hide It In are two applications that each allows the user to hide one photograph inside of another. Personally, I’m skeptical that a $0.99 app implements a sophisticated enough algorithm to remain undetected from a nation state, but it is probably good enough to fool a run-of-the-mill PI if used judiciously.
If you’re interested in something along the lines of free, that doesn’t require an app, check out Mozaiq to encrypt any image on your hard drive and even assign it a password. To decrypt an image, simply visit this link.
The reality is that modern steganography techniques are far more superior to replacing every n bytes with a character, or ending a sentence with or without an extra space. Each pixel is comprised of RGB values, or red-green-blue. In graphics circles, we describe them as bit planes. In effect, every picture can be reduced to its red plane, green plane, and blue plane–and there are other ways distill a photograph beyond this rudimentary example.
Imagine bouncing around, seemingly randomly, across the bit planes, changing a bit here and a bit there when encoding a secret message into a photograph. Detecting bit plane manipulation in an automated fashion is more difficult than detecting outlying pixel values–but steganalysis is possible.
Steganalysis
 Steganalysis is the practice of inspecting a medium to determine if it carries secret content. The Steganography Analysis and Research Center (SARC) focuses exclusively on steganography research and the development of advanced steganalysis products and services. According to their website, their clients range from the US Department of Defense, the CIA and metropolitan police departments. Suffice to say, as steganography advances, so do steganalytic techniques for detecting the use of steganography.
Steganalysis is the practice of inspecting a medium to determine if it carries secret content. The Steganography Analysis and Research Center (SARC) focuses exclusively on steganography research and the development of advanced steganalysis products and services. According to their website, their clients range from the US Department of Defense, the CIA and metropolitan police departments. Suffice to say, as steganography advances, so do steganalytic techniques for detecting the use of steganography.
Consider this ultra-simplified example of steganalysis. Histograms are two-dimensional graphs that show how many pixels in an image contain a certain value. Knowing that the range of a byte is 0 to 254, inclusive, a histogram iterates over every pixel in the image and looks at pixel brightness.
The resulting bar graph is typically used by photographers to determine the distribution of tones inside of the photograph, from the darkest on the right to the lightest on the left. Randomly changing n pixels to a character value could (theoretically) stand out in a histogram.
Steganography and Terrorism
 Right about now, you’re probably wondering if terrorists have considered using steganography to communicate among disparate cells. If you’re itching to read more about how terrorists might be using steganography, Wikipedia provides an interesting review of Alleged use by Terrorists.
Right about now, you’re probably wondering if terrorists have considered using steganography to communicate among disparate cells. If you’re itching to read more about how terrorists might be using steganography, Wikipedia provides an interesting review of Alleged use by Terrorists.
While irrefutable proof of modern terrorists using steganography is hard to come by, the reality is steganography isn’t new. In his excellent book The Codebreakers, David Kahn describes how German spies in World War II used steganography on a wide basis.
So, the next time you see a photo on Flickr–maybe, just maybe, the photograph isn’t really a photograph!
Editor-in-Chief’s Note: Be sure to check out our article main images from here on out on itstactical.com. We won’t be using passwords, but you’ll definitely want to give decrypting them a shot with Mozaiq. I’ve already said too much!