In my first article here at ITS, Social Networks and Your Digital Identity, the subject was identity theft.
One way to mitigate that risk is to carefully consider your privacy settings at social networking sites. Last week I presented the DefCon/Black Hat roundup, announcing a four-part series that inspects how ordinary things we take for granted encroach on our perception of privacy, much more so than opt-in social networking sites.
Today we’ll get into the first article in the data leaks series, how my car betrays me.
Data Leaks
I intentionally chose the term data leaks to describe the series over the phrase invasion of privacy. A data leak is like a faucet that is slowly dripping. At first blush, it doesn’t look like much, but over time it can add up to a significant volume. For our purposes, data leaks differ from an invasion of privacy because data leaks are preventable; they are passive, not active.
For example, you consciously choose to use a WiFi access point, and you consciously choose what data you wish to send over it by launching web sites, using email and IM, etc. An invasion of privacy is much more explicit, active, and intentional. The Great Firewall of China is a great example of an invasion of privacy, where Chinese citizens have no choice but to be monitored and censored by their government.
In a recent CNet article entitled Did we pronounce privacy dead this week?, Caroline McCarthy asks some provocative questions: does privacy exist anymore, and if so, do we even know what privacy is? I consciously chose to overlook the academic banter about what constitutes privacy in this series, lending yet another reason for my choice of the terminology data leaks. Frankly, I neither want to facilitate unnecessary alarm with this series, nor do I want to discourage people from embracing technological advances that increase the standard of living. After all, few would argue that the Internet and the web haven’t helped advance global communications.
The average citizen likely surrenders more privacy to employers than to the government. Employers routinely disclose that while at the office employees should have no expectation of privacy. Yet, how many of us regularly check personal email accounts at work, place an order at Amazon.com, or use the company phone to call home before leaving the office? More employers today require drug screening and access to our credit report than ever before. After all, it is their phone, their computer, their property–their rules. It is a sacrifice most make in lifelong pursuit of the greenback. Again, these aren’t the types of issues that this series is concerned with.
Toll Roads
 The demise of local and state revenues in the US has led to the rampant adoption of red light traffic cams and an increase in toll road construction. Generally, the intentions of these municipalities are pure, and the funds are used for much needed infrastructure management. Last year, Fox reported that there are over 5,244 miles of toll roads in the US, and drivers can expect more miles in the future. These local and state governments are not using the data to track the movement of the average citizen. What about hackers?
The demise of local and state revenues in the US has led to the rampant adoption of red light traffic cams and an increase in toll road construction. Generally, the intentions of these municipalities are pure, and the funds are used for much needed infrastructure management. Last year, Fox reported that there are over 5,244 miles of toll roads in the US, and drivers can expect more miles in the future. These local and state governments are not using the data to track the movement of the average citizen. What about hackers?
What is the data retention policy for these toll road authorities? I decided to look into three of the biggest toll way authorities, the North Texas Tollway Authority, Harris County Toll Road Authority, and Sun Pass, Florida’s toll way authority. I contacted the North Texas Tollway Authority and was verbally informed that they have a two-year statute to collect tolls. Harris County provides their customers with access to 18 months of history online. Why don’t these authorities openly disclose their data retention policies?
Black Market Data
Make no mistake about it; the black market pays a premium for personally identifiable information, sold by the megabyte. Even something that seems as innocuous as toll road records have value to a data mining hacker. The law firm of Pinsent Masons cited a 2007 Symantec report on the underground data economy: bank account data sells for up to $400 per account, passwords range between $1 and $350, and a one megabyte collection of email addresses costs between $2 and $4. Don’t be naive, hackers are collecting and selling daily routine data in addition to the more popular personally identifiable information.
Why is the data kept around for so long? Unfortunately it’s a tangled web–no pun intended. Most people link a credit card to their toll tags, and most municipalities accept credit cards as payment for tickets and fines. The credit card companies offer the consumer an extended period of time to dispute a charge on their bill. Therefore, entities like toll road authorities are forced to maintain toll road activity records much longer than what is actually needed. Realistically, there is no reason to keep the data around for more than a couple of months, but that just isn’t a legal option.
Reaffirmation
A hacker could easily establish someone’s daily routine by accessing red light cam networks, toll road databases, etc., gaining insight into when someone leaves home, when they leave work, etc. Let’s not even contemplate the ramification of a hacker accessing alarm monitoring company databases! If a hacker managed to gain real-time access to these systems, they could know someone’s every vehicular move–“He forgot to set his house alarm, he just got on the toll road at the Center Street on-ramp, and his refrigerator says it needs service.” Unrealistic? Hardly.
The Black Hat and DefCon conferences that ran during the last week of July in Las Vegas only reaffirmed what most probably suspect–the ability of a modestly trained hacker to gain access to such systems is too easy. For example, I heard first-hand reports from two separate conference attendees that the elevator system at the Riviera was hacked. Each told me that the elevator would stop in between floors and that a voice would come from the emergency communications speaker telling the riders to do something as trivial as hop on your left foot in order for the elevator to resume.
Las Vegas casinos are assuredly that wired, and someone found a hole in the system to have some fun.
Tire Pressure Monitoring System
 So what does this have to do with automobiles? Well, once again the best intentions of government have led to unforeseen data leaks. Remember the whole Firestone Tire/Ford Explorer fiasco from earlier in the decade? The US government passed the TREAD Act, mandating that new vehicles include tire pressure monitoring systems to advise drivers that their tires are not correctly inflated. European countries have similar laws. On the surface, it seems like an innocuous law, but dig deeper and you suddenly realize that yet another data leak has been created for the criminal digital elite looking to collect, categorize, and exploit personally identifiable information.
So what does this have to do with automobiles? Well, once again the best intentions of government have led to unforeseen data leaks. Remember the whole Firestone Tire/Ford Explorer fiasco from earlier in the decade? The US government passed the TREAD Act, mandating that new vehicles include tire pressure monitoring systems to advise drivers that their tires are not correctly inflated. European countries have similar laws. On the surface, it seems like an innocuous law, but dig deeper and you suddenly realize that yet another data leak has been created for the criminal digital elite looking to collect, categorize, and exploit personally identifiable information.
A tire pressure monitoring system (TPMS) is built into the valve stem, and vehicles generally integrate the system by collecting a short RF signal from each mounted tire, and perhaps the spare as well. If you’ve ever paired a Bluetooth headset with your cell phone, you can appreciate how the tires are paired with a vehicle. Unfortunately, the pairing of the TPMS with a vehicle requires specialized tools and software generally not accessible to the consumer. Most vehicles support 8 or 10 unique TPMS IDs in order to facilitate summer and winter tires without having to run back to the dealer to re-pair the tires.
These TPMS systems include a small watch-like battery designed to live between 7 and 10 years. Typically, they only transmit once per minute, or as frequently as every 5 seconds when the tire pressure is low. So what kind of data is included in these transmissions? Pressure level, battery level, and in some higher-end models information about the make, model, and tire position (e.g. passenger front) on the car. Finally, and here’s the kicker, every one of them include an unencrypted 32 to 108-bit globally unique identification number, depending on the make and model of TPMS.
A 32-bit number yields 4.29 billion unique combinations! Consider that there are 5 tires on the car, and suddenly we have a unique way to identify a vehicle remotely without looking at a VIN, checking a license plate, or even visually identifying the vehicle.
Exploits
Mike Metzger of Flexible Creations presented DefCon attendees with several DIY exploits. The first exploit discussed sending spoofed messages to confuse the car’s monitoring system–trick a driver into believing that they need to pull over because they have a flat tire. The second exploit was much more aligned with establishing an individual’s daily routine. “Near a stoplight, setup a sensor with a good antenna to grab the IDs/Formats of TPM sensors nearby.” Also described in the presentation, “Setup a network of receivers tied to loggers at given locations and track interesting vehicles going nearby.”
This first scenario is disconcerting–it’s late, remote road, single female driver, believes her right rear tire just went flat, feels compelled to pull over, “good Samaritan” a half-mile back stops to help, etc. The second exploit can lead to nefarious behavior as well. If someone manages to fingerprint a vehicle at work or home, they could easily setup discrete and inexpensive checkpoints to track that vehicle’s movement.
What can you do?
ITS is about being prepared and remaining vigilant. The idea behind this series is not to stir paranoia, but to educate. Prior to DefCon 18, I never thought about how much data could be gleaned from my vehicle when simply driving around. So what can be done about these vehicular data leaks?
In the spirit of the definition presented earlier, one consciously chooses to drive on a toll road. Likewise, one (sub)consciously interprets the yellow light to mean speed up, often running the red light and getting photographed in the process. Finally, with respect to TPMS, Firestone states that the Tread Act requires most vehicles made in 2006-07, and ALL made thereafter to be TPMS equipped. One consciously chooses to buy a brand new vehicle.
Let me preface this next statement–by no means am I advocating the disablement of a vehicle safety system. However, there is a subtle difference between equipped and enabled. Only 18 states and the District of Columbia have a periodic vehicle safety inspection program. According to the Texas Department of Public Safety vehicle inspection checklist, TPMS is not an inspected item, so if they are disabled the vehicle can still be driven legally, at least in Texas.
I certainly had no idea that my tires could give away my movements to someone actively looking to gather such details. Manufacturers will hopefully come to the realization that they only need about 16-bits to statistically ensure low odds that one car would inadvertently interpret another car’s TPMS transmission.
Closing
The lesson here is that hackers looking to make a buck by assembling a data package of personally identifiable information aren’t going to stop with a bank account or social security number. The more detailed of a profile they can create, the more valuable the data package is on the black market. Avoiding toll roads and buying a vehicle built in 1980 may not be an option, but at least now you have a better understanding of the data leaking from your daily commute.
Next week the series gets more technical, discussing just how fundamentally broken WiFi is… hope you weren’t reading this article over a Wifi connection!












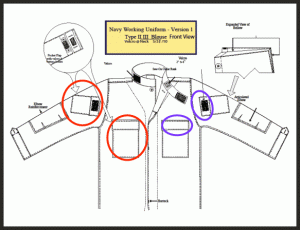
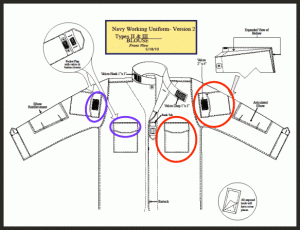
 There’s been a big buzz in the last few days about the newest Camouflage patterns available to the Navy and the Special Warfare Community. You may or may not be familiar with NWU (Navy Working Uniform) Type 1, 2 or 3, but we’ll attempt to clear that up and update everyone on what’s happening.
There’s been a big buzz in the last few days about the newest Camouflage patterns available to the Navy and the Special Warfare Community. You may or may not be familiar with NWU (Navy Working Uniform) Type 1, 2 or 3, but we’ll attempt to clear that up and update everyone on what’s happening.