This is the final article of the Inside Red Team Operations series, which is a walk through the Red Team process of planning, preparing and executing a security vulnerability assessment and penetration test; bad-guys style.
This is the final article of the Inside Red Team Operations series, which is a walk through the Red Team process of planning, preparing and executing a security vulnerability assessment and penetration test; bad-guys style.
Part 1 examined the elements and techniques necessary for planning the operation while Part 2 showed how information gathered during recon is used to implement the plan. This article uses the previous elements to show how the plan comes together.
Alright, we are ready. If you remember from the previous post, we were setting up a fake bird watching conference and expo. We bought the domain and built a basic website that provides information about the “expo.” We also have a C2 (command and control) server ready to receive any transmissions that our backdoors might send if we can install it on the target’s network. Now we just need a viable exploit.
Digging through all of the data we collected during our recon was a slow process, but it enabled us to discover several instances where IT personnel asked about specific versions of Windows, IIS and other applications. It’s a good start, but not enough. It’s time to start putting our social engineering skill to the test. We need to know what kind of operating system (OS) the Vice President or at least the majority of the users run so we can choose the perfect exploit.
I prefer redundancy so I’ll try an email approach and a direct approach via the phone.
First we craft our initial email to the VP of Marketing describing the conference and why we would like him to attend as a keynote speaker. We need to make this as convincing and official sounding as possible. Since we bought the domain for the conference we can create a convincing email address with a @conferencename.com in it. In the email we also point to “more information” on our website and we add snippets of comments from other “famous” bird watchers stating why the conference would be a success.
Before sending off this initial email, we need to write in a little bit of “code magic” to our website. It’s possible to retrieve the OS information through a code running in JavaScript. This code will be executed at the client side; the web browser running on the VP of Marketing computer or at least by his assistant. The code will then pass the information to another piece of code that is hidden from the user.
Now, the page we point to on the link is just a white page. There’s nothing on it other than a hidden use of the JavaScript code. Why? We are making sure that when we call and ask if they checked the website for more info, they would answer that the page was blank. We can then sound confused and ask what browser and OS are they running so we can “fix the page”… It’s all intentional.
Once all of this is ready, we can then send the email and one of two things will happen next:
1.) The VP or his assistant will open the email and go to the website. In this case we should have the OS and the browser information they used logged on our data dump.
or
2.) They don’t care and they will simply delete the email.
If the first scenario happens, we are good to go and we can choose to verify by calling them as a “follow up” to the email. This is optional, but I like to do it. Like I said, redundancy. If the second scenario happens, then we have no choice but to call them. In this case we need to be very careful as to not spook them. We want to sound friendly and convince them that this conference is going to be great and that it would be a privilege to have the VP as a keynote speaker.
So, the assistant opened the email and browsed to our website. We discover that she is running an old version of Windows XP without the latest service packs. It doesn’t surprise me. Now we can call and introduce ourselves. Another team member in the meantime is preparing the backdoor we want to install and the “weaponized” PDF that will make this happen. We call and of course she mentions that the webpage is blank. We can ask her what OS she is running and what browser is she using and tell her right there to try again. Of course we uploaded the actual page now so she can see it.
If we are lucky and she is friendly (shows interest) we can point her to the PDF we want the VP to read. This PDF “has useful information for the keynote speakers”. The PDF is a specially crafted document that will attempt to exploit one of two vulnerabilities found in the version of Internet Explorer that the assistant is running. Once this is exploited, the code will attempt to download the actual backdoor from our C2 server.
We can learn two things here: if the backdoor is downloaded successfully we then know that we can connect to the C2 server without any problems and that the security software on that computer didn’t detect us.
Of course, if the backdoor wasn’t successfully downloaded, it could be due to several reasons. The main two being that the exploit didn’t work or we were blocked and couldn’t connect to the C2 server.
Up to this point we were not sure whether we would need a physical penetration of the target. So, I’m going to divide the post in two now: what would happen if the backdoor was installed and what would happened if a physical entry is needed.

Digital Penetration
The weaponized PDF worked and now we have an initial entry into the target. We are now sitting inside the assistant’s computer. It’s tempting to start scanning for other computers connected to the same network, but we need to remember we wish to remain hidden and not be discovered. Our target is the VP of Marketing. Our focus should be him.
The backdoor we installed allows us to send other binaries that can help us recon the computer and eventually jump into the VP’s machine.
The first thing we do is install another, different, backdoor. This is done for redundancy and persistence. If the first one is discovered, we want to have another way in already in place. The second thing we do is to check the assistant’s email files. If she answered the VP’s email, she has access to his account. Maybe we don’t even need to access his computer to collect sensitive corporate information.
If we do need to jump on the VP’s computer, there are several things we can test. We can scan the network for the system names and see if we can spot this particular computer. This approach is usually noisy and can set off various alarms so it should be the last resort. If you do decide to go this way, create a very noisy piece of malware that will give IT and security something to chase after. While they are on the false trail, I’ll do a more silent scan of the actual network. Deception is key.
What I would start with is listing the shares on the Assistant’s computer. Maybe she is copying files to and from the VP’s computer. I would also check the list of past connections and the user names on her computer to see if maybe they are sharing the same computer. I could also send an email from her account to the VP’s and see if we can get the IP address from the email.
Moving inside the network is a delicate task. In our case we have a target, but what if we didn’t and we just want to find a possible target?

We are a red team, we need to think like an attacker. What are you after? Data? A specific computer or server? A specific person? Total disruption of the network? Once you know your target or what you want to achieve, make a plan. Create a diagram of what you know and what your next 4-5 moves will be. Create contingency moves for each one, you never know. It’s a useful thing to have when a good sysadmin or security guy on the other side discovered you and is trying to block you.
Modern networks, even in small to medium organizations, can have a lot of complexity and security features built in. Plan a stealthy recon and send a noisier bot somewhere else. Depending on how much time you have try to move slowly. Do not set off any alarms. Add each potentially good system you find to an overall map of the network as you know it. Record their names, IP address, OS, apps running, etc. The idea is to have as much information in front of you on the whiteboard as possible, then plan the next phase: where to go and what to extract. Plan the egress routes and the protocols you’ll use to extract the information. In our case, we can setup a good backdoor with a connection to the C2 server but sometimes extracting the information is not as easy. You should get different servers ready to receive the data (encrypted of course since it’s property of your customer). Have fallback servers as well; Mr. Murphy is always present.
Once you are done with the planning, execute. Again, stealth is key here. Unless you were specifically hired to test the reaction of the organization’s quick reaction teams, you should try to be as quiet as sign language. Move slowly and copy information in small bits. If you have a 2GB file you need to extract, partition it into smaller chunks and extract them using different protocols.
When you are done with the execution, vanish. Clean any backdoors and other tools you might have left on the network. This is done not only to avoid being detected, but if there is an actual bad guy in the network you don’t want to aid them with tools or backdoors. Do not erase logs. These are great educational tools for the security guys at the organization and they can learn forensics through them.
So, back to our target, the VP. Searching for a share or a connection didn’t return any leads. We can however send an email to the VP with the link to our website where the JavaScript code can grab his IP and other information. Using the Assistant’s email address we send him an email saying that she thinks the keynote invitation is a great opportunity and he should check out the website. This works. We now have the IP address for the VP’s computer.
By using a small port scanner (using a custom low-signature port scanner we wrote and uploaded via the backdoor) we discover that the standard Windows administrative shares are enabled. These are the classic C$, D$, ADMIN$, etc. These shares will allow you to browse the computer’s files remotely by doing a simple \\IP_ADDRESS\C$ (it’ll display the contents of the C:\ drive). In some cases these shares require login credentials, which are relatively easy to get by “sniffing” the network or grabbing them out of the domain controller (this is a subject for a whole different post…). So, we move into our target and after a quick search we find his documents. We compress them, partition the file into smaller chucks and began the slow and methodical process of data egress.
An offline analysis of the documents reveals that we now have a copy of the corporate marketing plan for the next 5 years.
Mission successful.
Physical Penetration
Sometimes a digital-only penetration is not possible. Ultimately we would still like to get those valuable documents but we can’t find a way in through the exploitation of digital vulnerabilities. This is when the physical recon we did in the early stages of the project comes in handy.
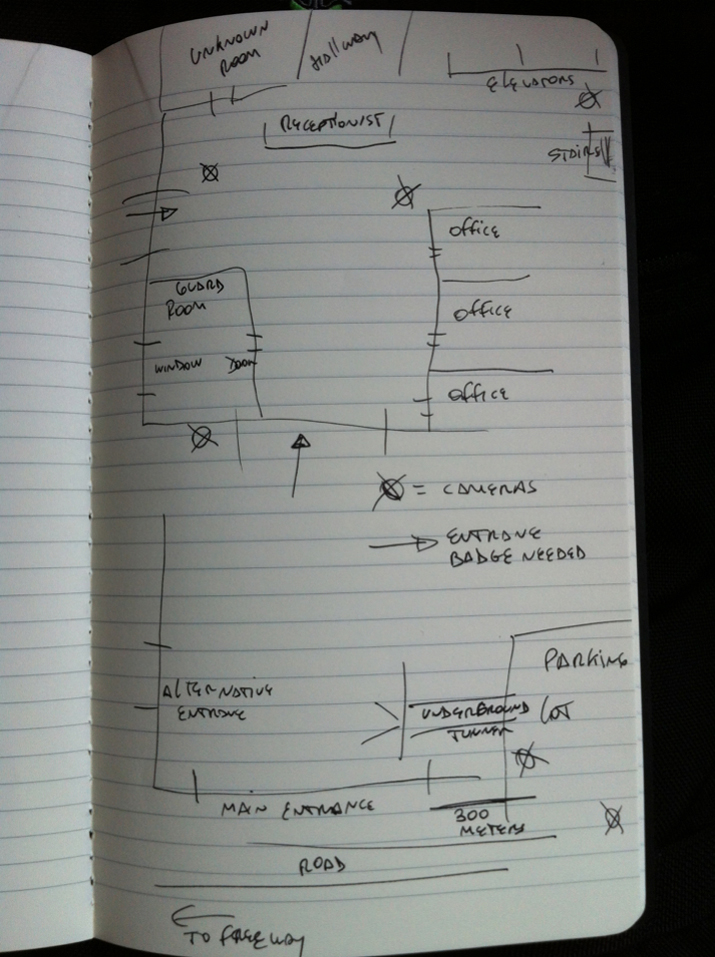
There are two types of physical penetrations: covert and overt. In a covert infil you find a way to breach the physical security of the perimeter and enter the premises without anyone knowing you were there. An overt infil, on the other hand, is one where you enter the building in plain sight, go through security and pretend to have a reason to be there. I’ll focus on the overt case because usually these are the most fun.
We first need to come up with a plausible backstory. Just as before, believability is paramount.
The company uses Software X to run its servers. X is a very expensive piece of software that requires a very specific license. It is known that big companies try to save money by acquiring one license and reusing it on more than one server (illegal). One scenario I found that often works is the guise that I am there to check their licenses. How can we do this?
Based on experience, security guards and receptionists at the main entrance of the company are often bored and tired, so a well placed call a day or two ahead of the operation will give us a good way to get in. We call and we can say something like: “Hi, my name is John Doe, I’m with Software X. We are currently performing our quarterly license test and we’ll be sending Mr. Some Name tomorrow to check yours.” Now, in some cases the security guards will transfer this call to an IT engineer or manager in charge of the servers. These people can challenge this by saying that they would talk to their Software X account representative and that’ll be the end of it. If you really did your homework you would have called Software X and asked to talk to the person in charge of this account, so you would know his name. You can tell the IT person that “Mr Account Manager Name” is up to speed and he would be calling him soon to let him know about the license check.
Most times, the security guards will eventually let the IT person know, but in a way so out there that the IT person would go something like: “OK, let me know when he is here.”
Now, I usually use a name I can back up with an ID. Either my real name so I can show them my drivers license, or one that I can have a fake license made. I also like to have an ID card with the logo of the company I’m supposedly working for, together with my name, picture and other little pieces of false info. You can find pictures of badges by searching for them online. It doesn’t have to be perfect, but it has to be good enough to make the guard believe you indeed are an employee of Software X.
This way, when we arrive in the building the next day, they are expecting us. We need to be dressed properly, suit and tie, etc. Go to the guard, give them your name and the drivers license and fake Software X ID card. Tell them you are here to check the license. Chances are you will be told to wait for the IT person to show you in. When that person arrives, introduce yourself, show them your ID card or give him a fake business card. You can mention “Mr Account Manager Name” and share that he sends his regards. Make it sound official.
If you are lucky you will be let into one of the server rooms. If you get to this point you are done. It would take little work to get to the good stuff from there.

If this first deception didn’t pan out as planned, there are other methods of overt infil you can attempt. Again, dressing up and playing the part is key. You need to arrive first thing in the morning, when everyone gets in. Try to find the smaller entrances, one that would get less attention by the security guard and just walk right in pretending to be on the phone. Hang a fake ID card on your pocket with the rear of the ID facing outwards. If someone is looking at you, they will see a badge and most likely won’t bother you (since you are also “on the phone”).
Once inside, you need to do a little recon and find those servers. Depending on what intel you gathered from your initial recon, you may actually have a pretty good idea of the servers location.
At this point I like to talk to the cleaning people if I can find them. I become very friendly with them, speaking in their own language if I can, talking about sports or other things you might notice on their cleaning carts, clothing (logo hat, uniform or t-shirt, etc) and other stuff. Once you have that conversation going, you could steer it towards something you want to know, like: “Wow, this is a huge building. How do you manage to take care of it by yourself?” He would reply: “Oh there’s a whole group of us that clean here.” Then you can go: “I bet they have the biggest computer rooms!” He at this point is your friend and chances are he would answer something like”: “Yeah, the room on the 3rd floor has 200 computers! It takes the whole floor.” Bingo, you have the info you were looking for.
It’s not always that easy, but you get the idea.
Physical penetration can be dangerous, especially on companies where the guards are authorized to use lethal force to stop an intruder. I’ve been there and have almost gotten shot a few times.
Anyway, this is in my opinion the most fun part of the project, however it should be your last resort. Training often and hard is the key. Go out and play safely.
Editor-in-Chief’s Note: U. Fridman is a senior information security consultant that specializes in detection of information security threats and response to security incidents. His background includes extensive experience in red team activities and management, information warfare, counter cyber-terrorism, industrial espionage, forensics analysis and other security services.













 The ability to speak a second language is becoming an increasingly important skill-set. There are many ways to learn a language, from the not-so-good (software-based), to the best (immersion). This article should be used as a starting point to develop your skills in the Spanish language, but should not be your only resource. Interaction with native speakers, television, movies, radio shows and constant practice, should all be part of the learning process.
The ability to speak a second language is becoming an increasingly important skill-set. There are many ways to learn a language, from the not-so-good (software-based), to the best (immersion). This article should be used as a starting point to develop your skills in the Spanish language, but should not be your only resource. Interaction with native speakers, television, movies, radio shows and constant practice, should all be part of the learning process.
 This is the final article of the
This is the final article of the