
I’ve recently finished reading a book by Gavin De Becker called The Gift of Fear. While book reviews are something we don’t often cover on ITS, this is a book that I not only feel each of you should read immediately, but that every member of your family should read as well.
This is hands down, one of the best books I’ve ever read and the most applicable to any of the skill-sets we advocate here on ITS. Primarily, what we all encounter on a daily basis, fear of the unknown.
De Becker describes this fear of the unknown as unwarranted and a curse, while advocating true fear as a gift. This book explains how to tell the difference between the two and teaches us how to trust and act on our gut instincts. This book could truly save your life!
Gavin De Becker
I’d like to take a paragraph to introduce De Becker and what makes him an authority on the subject at hand, because like you, I was skeptical until I started reading the book, which has become a bible for me personally.
“Gavin De Becker is a three-time presidential appointee whose pioneering work has changed the way our government evaluates threats to our nation’s highest officials. His firm advises many of the world’s most prominent media figures, corporations and law enforcement agencies on predicting violence and it also serves regular citizens who are victims of domestic abuse and stalking.
De Becker has advised the prosecution on major cases, including the O.J. Simpson murder trial. He has testified before many legislative bodies and has successfully proposed new laws to help manage violence.”
His biography might read well, but I’m here to tell you that this doesn’t even scratch the surface of what information he brings to the public with The Gift of Fear or what his organization, Gavin De Becker, Inc., has done to help through their vast resources and organizations they support.
The Gift of Fear
Around two years ago I wrote an article titled Dealing With Violent Confrontations and have even recently shared my experience with a fear inducing incident of my own. What I have always and will always advocate, is trusting your gut (i.e. listening to your instinct.)
I picked The Gift of Fear up after the recent incident I mentioned, because I wanted to learn more about what I experienced and how I handled the situation. While I had a lot of supportive comments and people sharing stories of their own fear inducing experiences, there were also many that wrote it off as nothing more than American paranoia.
Through reading The Gift of Fear, I’ve found an authoritative voice stating that I did exactly what I should have in that incident. Put manners aside, quieted my mind and listened to my instinct. While it’s hard to address feelings and emotions, let alone instinct, in the article I described my response to an unidentified man who quickly and feverishly approached my personal space. I’ll let you read the article for yourself if you haven’t yet.
De Becker describes listening to your instinct as law and that if you’re constantly living in a state of fear and paranoia, you won’t be able to hear your instinct in the situations where it’s warranted and trying to save your life.
There’s a fantastic comparison in the beginning of The Gift of Fear that really brought things into perspective for me. De Becker relates the intuition of humans to animals. Our intuitive abilities are superior to that of animals and that we’re in top form because we add to our experiences every day. The thing about animals is that we as humans have something extra that they don’t; judgement.
It’s also that thing called judgement that gets in the way of our perception and intuition. It causes us to disregard our intuition unless we can explain it logically, rather than honor it. No animal in the wild would suddenly be overcome with fear and spend their mental energy thinking that it’s probably nothing.
Unfortunately, De Becker describes our initial response as writing off the feeling of someone’s unusual behavior being sinister as being paranoid instead of appreciating the powerful internal resource. We rush to ridicule the impulse, especially in others, as witnessed by the comments in my article.
“We, in contrast to to every creature in nature, choose not to explore – and even to ignore – survival signals.”
Violence for All
Something that I also sat up and took notice of is that De Becker states that people who commit terrible violence choose their acts from among many options that we’re all capable of imagining.
Just the fact that we’re all capable of being able to conceive terrible violence is evidence that anyone can do the same, even those willing to act on it. The real lesson from De Becker in this situation is that to work towards prediction and prevention, we have to accept that these acts are done by the “we” of humanity not by interlopers who somehow sneaked in.
Something we’ve also been seeing first hand in the news reports from the Aurora tragedy, are interviews from people who knew James Holmes as a quiet guy, or someone who kept to himself. De Becker talks about this too as a hackneyed myth and that a more accurate statement should be “neighbors didn’t know anything relevant,” but instead news reporters present non-information as if it’s information.
De Becker states that by the frequency of this cliché, you could almost believe that normalcy is a pre-incident indicator for aberrant crime. It isn’t. However, one of the most common pre-incident indicators, is violence in one’s childhood.
Predicting Violence
Predicting stranger-to-stranger crimes is based on a few details, as De Becker describes, but even the simplest form of street crime is preceded by a victim selection process. These can include being the right appearance or “type” and generally outside the victim’s influence. I would add though that being a harder target will also cut down on allowing yourself to appear to be the right type.
De Becker breaks this down too into conditions that make someone available to a criminal and that are completely within our control. For example, accessibility, setting and circumstance. “Will you engage in conversation with a stranger when you’d rather not? Can you be manipulated by guilt or the feeling that you owe something to a person just because he offered assistance? Will you yield to someone’s will simply because he wants you to, or will your resolve be strengthened when someone seeks to control your conduct? Most importantly, will you honor your intuition?”
Intuition falls right back into predicting violence and it’s always learning. De Becker states that some signals it sends may occasionally be less urgent, everything is meaningful and unlike worry, it won’t waste your time.
Living in Fear
De Becker explains that fear is something that surrounds us always, but walking around in a constant state of vigilance can misinform your intuition about what really posses danger. This is something I digested very carefully, as I take situational awareness very seriously and still do after reading this book. I don’t consider my situational awareness as being hyper vigilant either, I feel it’s balanced well and that I’ve refined it even more after De Becker’s advice.
Honoring accurate intuitive signals and evaluating them without denial (believing that either favorable or unfavorable outcome is possible,) you need not be wary according to De Becker, for you will come to trust that you’ll be notified if there’s something worthy of your attention. Fear will gain credibility because it won’t be applied wastefully.
“When you accept the survival signal as a welcome message and quickly evaluate the environment or situation, fear stops in an instant. Thus, trusting intuition is the exact opposite of living in fear…While few would argue that extended, unanswered fear is destructive, millions choose to stay there. They may have forgotten or never learned that fear is not an emotion like sadness or happiness, either of which might last a long while. It is not a state, like anxiety. True fear is a survival signal that sounds only in the presence of danger, yet unwarranted fear has assumed a power over us that it holds over no other creature on earth.”
De Becker lists two rules about fear and that if you accept them, they can improve your use of fear, reduce its frequency and transform your experience of life.
- Rule #1. The very fact you fear something is solid evidence that it is not happening.
- Rule #2. What you fear is rarely what you think you fear, it is what you link to fear.
Rule #1 couldn’t be any more true. How many times have you lied there in bed thinking about what would happen if someone was standing over your bed right now with a gun. Guess what, the thought is precisely all the evidence you need to know that very thing you fear is NOT happening.
The second rule is one that needs a little explanation from De Becker. His example is the fear of getting up and addressing five hundred people at an annual convention. The fear is not just the fear of embarrassment, it’s linked to the fear of being perceived as incompetent, which is linked to the fear of loss of employment, loss of home, loss of family, your ability to contribute to society, your value, in short, your identity and your life.
When you truly analyze what it is you fear and it’s chain of causality, it can help alleviate that fear or let you know exactly what you need to change to alleviate it.
Other Topics
Some of the other great topics De Becker address in The Gift of Fear are workplace violence and the pre-incident indicators surrounding it and help in predicting it. There’s also fantastic help-giving resources near the end of the book, such as questions you should be asking your child’s school.
For example, are background investigations performed on all staff? Are acts of violence or criminality at the school documented? Are the statistics maintained? May I review the statistics?
There is one part in the book’s appendices that talks about gun safety and this is the only part of the book that I don’t completely agree with. Rather than discuss it here, I’ll leave it up to you to review it yourself.
Again, I can’t suggest enough that you and your loved ones read this book. Even if your spouse doesn’t share the mindset you do, The Gift of Fear does an excellent job of speaking directly to everyone, regardless of their mindset, preconceived notions or beliefs. I implore you to find the time to purchase and read The Gift of Fear, I can’t think of a better way that a few hours and ten bucks could transform your life and potentially save it.







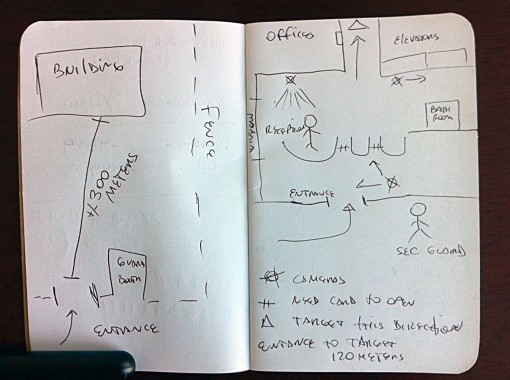
 In this three part series we’re going to go through what it takes to perform a security vulnerability assessment that would ultimately end in the penetration of the target.
In this three part series we’re going to go through what it takes to perform a security vulnerability assessment that would ultimately end in the penetration of the target.






 In one of the deadliest U.S. shootings since Fort Hood, where Army psychiatrist Nidal Hasan fired into a group of soldiers preparing for deployment, James Holmes killed 12 innocent movie-goers Friday, when he began shooting into a crowded theater in Aurora, Colorado.
In one of the deadliest U.S. shootings since Fort Hood, where Army psychiatrist Nidal Hasan fired into a group of soldiers preparing for deployment, James Holmes killed 12 innocent movie-goers Friday, when he began shooting into a crowded theater in Aurora, Colorado.
 The first thing I did when putting on the gloves was to get the gloves and my hands wet. They come dusted with food-grade corn starch for easy donning in a non-water environment such as sky diving, but for water, they recommend submerging the glove to don them.
The first thing I did when putting on the gloves was to get the gloves and my hands wet. They come dusted with food-grade corn starch for easy donning in a non-water environment such as sky diving, but for water, they recommend submerging the glove to don them.



