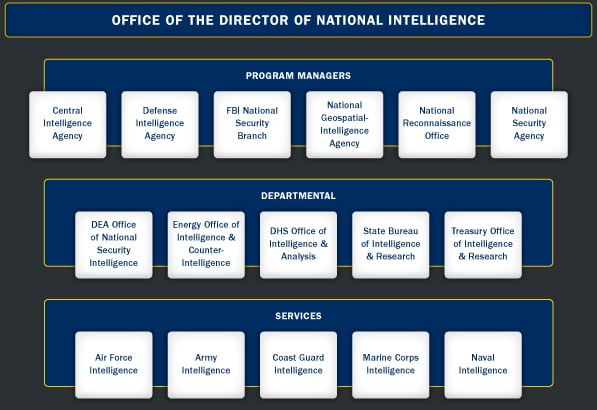
When I first considered entering the intelligence community (“IC”), the notion of classic Cold War-style cloak and dagger espionage was enthralling. Good guys versus the bad guys; the brutal hand of the USSR versus the liberating forces of the United States and democracy. Scenes of car chases, meetings in safe houses, or exchanging coded messages in city parks, coffee shops, or in passing on a busy sidewalk were the dreams of intelligence operations that I envisioned.
But a few pieces of the puzzle were missing, pieces that will be explored in this article.
As mentioned in Part 1 of this series, there is a difference between information and intelligence, as well as a process (or a cycle, as it is referred to) by which intelligence is delivered from the source, analyzed and passed to the customer for consumption. This process varies from agency to agency but is most commonly referred to as the TCPED*, or intelligence cycle.
The purpose of this article is to introduce this cycle, as well as to highlight the most critical aspect of intelligence as a function in regards to providing useful information to customers: analysis.
The Intelligence Cycle
TCPED is the cycle through which timely, accurate and relevant information is made useful and available to consumers and operations.
T – Tasking
C – Collection
P – Processing
E – Exploitation
D – Dissemination
TCPED outlines the general pipeline through which information passes via the various entities within the IC. While each of these steps occur virtually simultaneously and across the entire spectrum of strategic/national, operational and tactical levels of the IC, the general cycle remains identical for practical purposes.
For the sake of time management and everyone’s sanity, the individual steps of the TCPED process will not be explored in this article (possibly at a later time). The most important thing to note is that it is a continuous, dynamic and massive scope of activity that requires constant administrative, operational and resource-intensive focus across all levels of the IC.
So what then in the intelligence cycle is most important for the IC in providing timely, accurate and relevant information to consumers? Well here’s a hint — it’s only implicitly mentioned in the TCPED cycle: analysis. Just as the intelligence cycle is a continuous, dynamic and massive activity that requires constant oversight and management by the IC, analysis is just as omni-present and equally as important.

Analysis
Analysis is to intelligence as oxygen or blood is to life. Without it, consumers are left only with raw information or facts, depleted of perspective, insight or purpose. As paraphrased by Miriam-Webster, analysis is the process of breaking down a complex issue or matter into smaller parts or components in the hope of gaining a better understanding of the issue.
In the context of intelligence operations, analysis is the process of taking often incomplete, missing or complex information and breaking it down into a product that provides unique and valuable insight (which is also timely, accurate and relevant if done correctly) to the customers.
Scenario
To highlight the importance of analysis, let’s say you are planning a hiking trip to the mountains and are told prior to leaving to research the weather**. You enter the word “weather” into Google (without having any local or personalized settings set) and are told the sky will be blue and clear, nothing further. At this point, you have information without analysis — just raw facts. You have no context, no perspective and the information really has no value because it has not been broken down or processed in a form that fits the context of your hiking trip.
Contrarily, let’s say some analysis was performed, and compare the results. More research was conducted, given context, and tailored to your hiking trip specifically. Where is the trip taking place? Where will you move from your starting point? What altitude will you be hiking at? What historical weather data for the location is available? Have any hikers hiked in the same location at the same timeframe in the past? These are just a sample of the questions that would need to be asked in order to analyze what the weather will most likely be for your hiking trip. Sounds simple, right? Look into the past, find any relevant historical data, and apply some context in order to make it relevant to your situation. Well, almost. Let’s look at a strategic example.
What happens when the situation and environment become more complex? Instead of the weather, you’re trying to determine when one leader of an aggressive country is going to decide to order his military to assault its neighbor in order to seize its abundant supply of natural resources. Well, we cannot read minds yet or this problem would be easy.
What we can do is watch everything else: the leader’s movements, the position, activity, and movement of various units the leader may use to conduct an assault, monitor any weapon systems that could be used during or prior to an assault, or maybe assess which other key events may provide policymakers with some forewarning of hostile action. But how do you assess what you’re seeing is forewarning of an attack? You need a baseline. Which means you’d need to be monitoring this country and its activity well before you believed the leader had any intent to invade his neighbor. You must establish what is normal before it becomes abnormal. So the plot thickens.
Informed Decisions
Without intelligence, and specifically analysis of available information, none of this would be possible. There would be no baseline, because no one ever thought to establish one, because no one possessed any context or perspective of that country or region. Even if all of the above information was known, analysis is still required. What historical precedence or trends are available? What other information regarding the leader or his country is available, and how can it be applied to the current situation? Context, perspective, and insight relative to the situation is still required in order to even begin to properly assess the hostile leader’s possible actions.

It should be obvious (hopefully not too much so at this point) the role that analysis — and professional analysts — play in the intelligence cycle and IC. Without analysis or trained human analysts to process intelligence, there is only raw information. Context, perspective and an application of what is known must be applied to the situation in order to begin to understand that which is unknown.
It is the complexity and dynamic nature of world events that ensures intelligence analysts are never short of work. Without them, it would be impossible to sift through the ambiguous, conflicting, or missing pieces of the puzzle that policymakers require in order to make the correct, informed decisions.
In order to address various scenarios like this every day and to provide timely, accurate, and relevant intelligence to US policymakers, there are a number of analytical techniques that can be employed by analysts during the TCPED cycle. A few of them can be found below.
Analysis is the bread and butter that allows analysts to turn raw information into timely, relevant, and accurate intelligence — intelligence that has been properly applied and contextualized throughout the TCPED cycle. It is a critical component of what the IC does, and is performed in order to assist policymakers, enable operations, and to ultimately ensure the survival and safety of the United States.
Footnotes
- *TCPED is most commonly applied to Intelligence, Surveillance, and Reconnaissance arena but can be applied to the scope of general intelligence operations as well.
- **The weather example is somewhat ironic because weather forecasts are a product of analysis themselves, based on trends and most likely courses of action of atmospheric conditions, etc.
- ***This document provides an excellent primer on intelligence analytical techniques: [pdf]
Editor-in-Chief’s Note: Oscar M. is a Junior Active-Duty Intelligence Officer supporting a conventional airborne-capable unit. “My goal is to serve by protecting the US Constitution, keep the bad guys of the world at bay, fighting them when necessary and ensuring that the American people don’t have to.”